We provide
Threat intelligence analysis
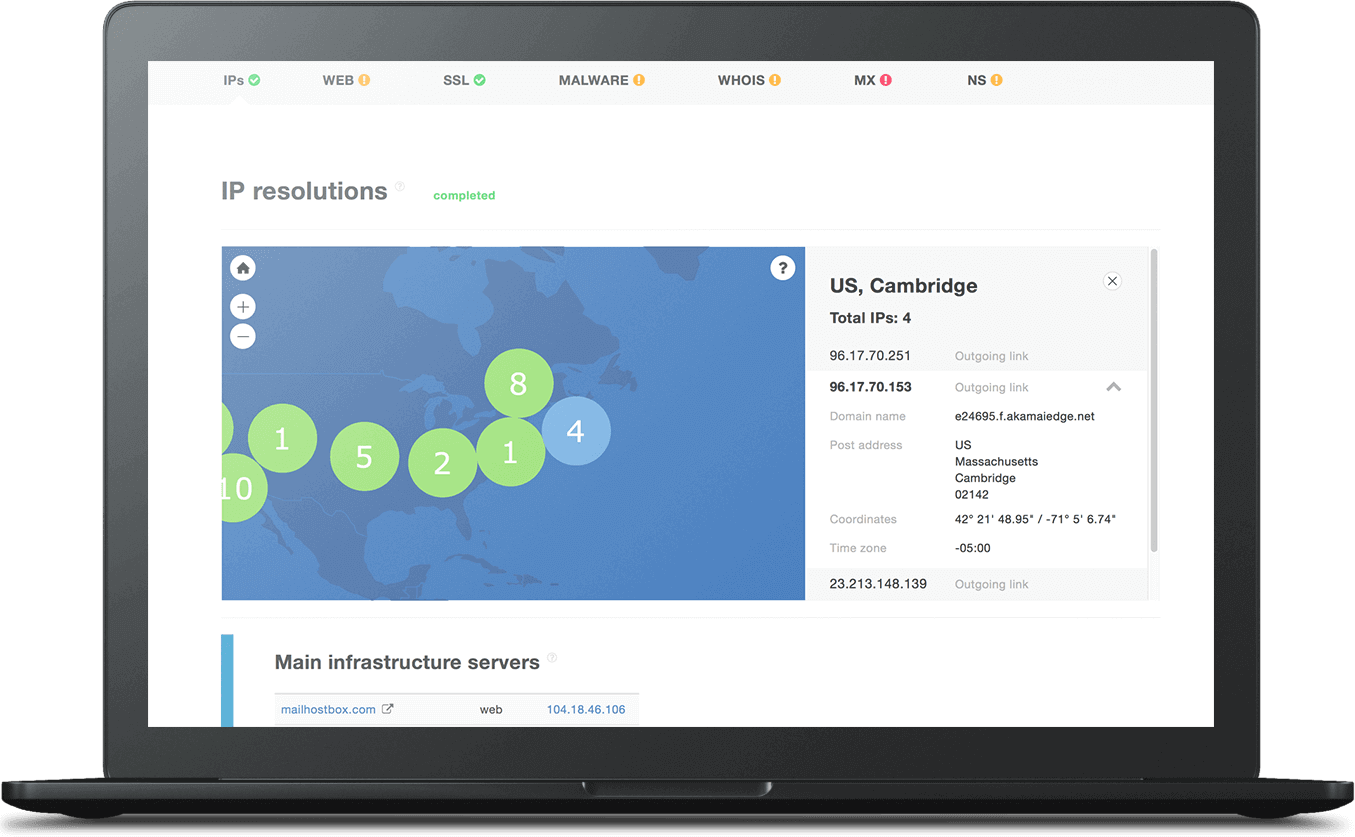
Find detailed information about a host and its underlying infrastructure in seconds through the Threat Intelligence Platform web interface.
Sample reportsThreat intelligence APIs
Integrate our rich data sources into your systems to enrich results with additional threat intelligence insights.
Available APIsMain use cases
Integrate our capabilities into existing cybersecurity products, including cyber threat intelligence (CTI) platforms, security information and event management (SIEM) solutions, digital risk protection (DRP) solutions, and more.
Use our reports and APIs as additional information sources on yet-unidentified indicators of compromise (IoCs) such as domain names, IPs, and Domain Name System (DNS) records.
Third-party systems, solutions, or services can cause your network harm should these be found vulnerable. Assess the reputation of external partners, clients, and other third parties extensively by subjecting their digital assets to great scrutiny.
Reduce your potential attack surface by subjecting all digital properties to comprehensive checks for vulnerabilities, dangling records, misconfigurations, or malware database listings.
Given a single network identifier (a domain name or an IP address), examine other related web properties that can pose threats to your network.
Reduce risks coming from unforeseen weaknesses in your digital infrastructure. Put your Secure Sockets Layer (SSL) certificate and SSL certificate chain to the test by identifying potential loopholes that threat actors can abuse.
Sample reports
Threat intelligence APIs
Domain's Infrastructure Analysis API
For a given domain name, get a collection of its web, mail, and name servers as well as its known subdomains. For each infrastructure entry, find out its IP address, geolocation and subnetwork information.
Read moreSSL Certificate Chain API
For a given domain name, get detailed information about its SSL Certificate and the complete SSL Certificate chain. The data is provided in a unified and consistent JSON format and could be easily integrated with your system.
Read moreSSL Configuration Analysis API
For a given domain name, establish and test SSL connection to the host and analyze how it is configured - to detect common configuration issues potentially leading to vulnerabilities.
Read moreDomain Malware Check API
For a given domain name, check if it is considered to be dangerous in different security data sources. Dangerous domains could be related to a malware distribution network or host a malicious code.
Read moreConnected Domains API
Retrieve a list of domain names resolving to a given IP address, including subdomains. Make sure the website does not share the IP address with malicious domains, as that may result in overblocking – a situation when a blocked malicious site also blocks other sites with the same IP. Research the infrastructure of connected domains.
Read moreDomain Reputation API
Evaluate a domain's reputation based on numerous security data sources as well as on an instant host's audit procedure. For a given domain name or IPv4 address, collect and evaluate over 120 parameters and calculate the resulting reputation score.
Read more
You're just a step away from getting a free and fully functional trial!
Try it freeNo credit card or company information needed.
We check
IP Resolution
Analyze a host’s infrastructure and get related IP addresses along with their geographical / Autonomous System (AS) details for comparison with reverse IP lookup results.
Read moreSSL Certificate Chain
Analyze a domain’s SSL certificates, test their SSL connection, and check their configuration.
Read moreWebsite Content
Perform a content analysis to determine relationships with other domains and flag host configuration issues.
Read moreMalware Detection
See if a domain or IP address has been cited for malicious activity in any of several connected third-party threat data feeds.
Read moreMail Servers
Check a domain’s mail exchanger (MX) records for configuration issues and identify its corresponding mail servers.
Read moreNameservers
Check a domain’s nameserver (NS) records for configuration issues and get a list of all its NSs.
Read moreGive the platform a try!
No credit card or company information needed.
Have questions?
We work hard to improve our services for you. As part of that, we welcome your feedback, questions and suggestions. Please let us know your thoughts and feelings, and any way in which you think we can improve our product.
For a quick response, please select the request type that best suits your needs.
Threat Intelligence Platform uses cookies to provide you with the best user experience on our website. They also help us understand how our site is being used. Find out more here. By continuing to use our site you consent to the use of cookies.