Cybersecurity is indeed a growing concern for all. Over the years, we continued to witness a considerable increase in the volume and sophistication of cybersecurity threats — resulting in breaches, 28% of which were malware-enabled, which continue to cripple companies. Amid this backdrop, cybersecurity experts must remain vigilant and ensure that none of their network-connected systems are malware-infected.
In this post, we take a look at how threat intelligence tools like Threat Intelligence Platform (TIP) can help them safeguard their infrastructure from debilitating attacks. Before that, though, let’s list some of the most common malware-enabled cyber attacks that cybersecurity teams must thwart.
4 Threats Every Organization Needs Protection From
When it comes to cybersecurity, defenders first need to know how attackers get into their networks. These days, the latter typically exploit vulnerabilities in software and hardware with malware. We identified four ways in which malware infection can start in a target network below.
1. Phishing
Phishing is one of the oldest cyberattack methods that remain effective to this day. Attackers usually prey on the fear or shock of victims to get them to click on malicious links embedded in an email or download a malware disguised as an attachment. Such was the case in a recent Amazon Prime phishing campaign. Targets received emails telling them they were locked out of their accounts and thus needed to verify their details to continue using the service. While this particular campaign looks like a test easy to foil, users should always be wary of phishing that often tricks them into handing out their account or payment card credentials to cybercriminals.
2. Malware
Most malware campaigns often ride on trending topics that are likely to get victims to visit a malicious site where the file automatically gets dropped onto their computers. The point is to run some harmful computer program the user is not even aware of. In some cases, attackers use emails to spread mayhem: even document attachments can contain executable code running automatically upon opening. That was how attackers went about distributing Emotet Trojans in the guise of documents that provided important information about the ongoing Coronavirus outbreak.
3. Unauthorized Command and Control
Some of the malware is distributed by cyber attackers to find vulnerable computers to make them part of their botnet. Bots or zombies then figure in attacks against big targets, forming the most important infrastructure at the miscreant’s disposal. The so-called “Winnti Group” is infamous for turning the systems of insufficiently protected organizations in the healthcare and education sectors into bots using the ShadowPad backdoor. A backdoor, of course, is a type of malware that allows attackers to control and command infected computers remotely. They then use these compromised systems to launch attacks against video game and software companies.
4. Denial-of-Service (DoS) Attacks
The biggest distributed DoS (DDoS) attack to date is still the one against GitHub. A 1.3Tbps-strong attack flooded its network, causing the organization to go offline for five minutes, although a complete recovery took nearly a week. DoS attacks cause victims to lose revenue due to site unavailability.
As shown, these four types of attacks can cripple victims, making it all the more necessary to defend against them. With this in mind, TIP can identify known spam senders and disreputable sites. Threat intelligence analysis can help organizations reduce their exposure to malware-instigated attacks. Read on to find out how.
Performing Threat Intelligence Analysis with Threat Intelligence Platform
TIP allows users to scan their web properties for any sign of malware infection, thus reducing their chances of suffering unwanted consequences. It specifically:
1. Checks Domains for Ties to Phishing
Users can run all domains that wish to interact with their IT infrastructure on TIP before granting them access. Say, for instance, that an employee gets an email from a sender sporting the domain 4black4[.]pro. When queried on TIP, they can see that the domain is listed on PhishTank (a publicly accessible phishing blocklist). It is also a known malware host based on VirusTotal (a public threat database). That said, all access coming from and going to any site on the domain should be blocked.
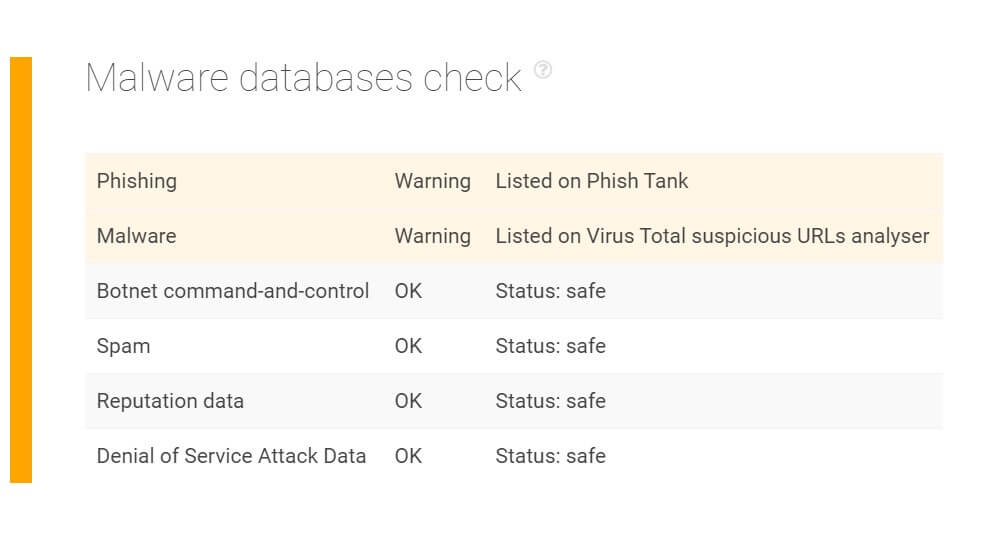
2. Determines If Sites Are Known Malware Hosts
TIP checks if any of the sites interacting with a network contain malware. It runs them through several databases that include Google Safe Browsing, Yandex Safe Browsing, and VirusTotal Suspicious URLs analyzer, among others.
We tested it on the known malware host http[:]//hodermouse[.]com/hotoffice/ and found that it was on both VirusTotal and Google Safe Browsing. Apart from blocking access to and from the site, it is also a good idea to prevent any communication with the domain hodermouse[.]com. The page may not have been the only one that the attackers compromised.
![We tested it on the known malware host http[:]//hodermouse[.]com/hotoffice/ and found that it was on both VirusTotal and Google Safe Browsing. Apart from blocking access to and from the site, it is also a good idea to prevent any communication with the domain hodermouse[.]com. The page may not have been the only one that the attackers compromised.](https://publishing-platform.threatintelligenceplatform.com/wordpress/wp-content/uploads/Copy-of-image-2.jpg)
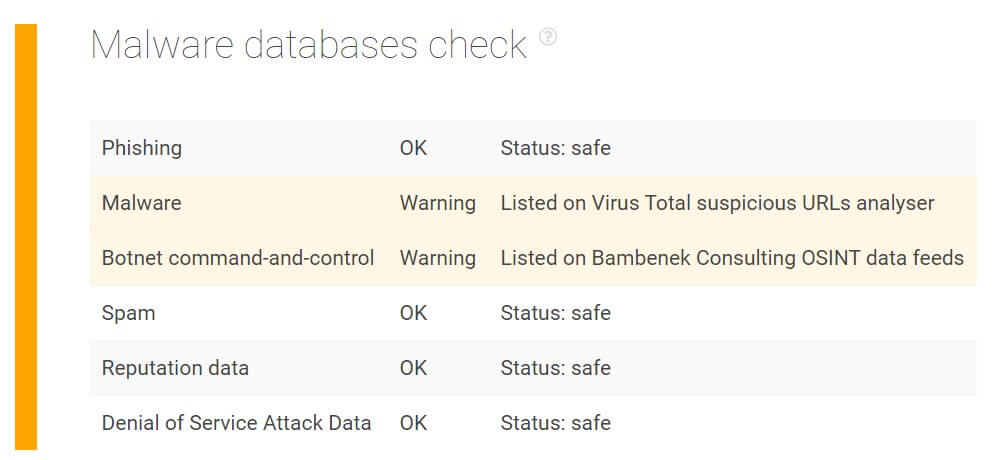
3. Warns About Command-and-Control (C&C) Server Connections
TIP can also notify users about URLs that have ties to known C&C servers. It pulls results from the Zeus Tracker, the Ransomware Tracker, and Bambenek Consulting OSINT data feeds, to name a few.
We ran the known C&C server domain afapudcvknpewfc[.]com on the platform and found that it was on both VirusTotal and the Bambenek Consulting OSINT threat repositories. Blocking access to and from the said domain should thus be done immediately.
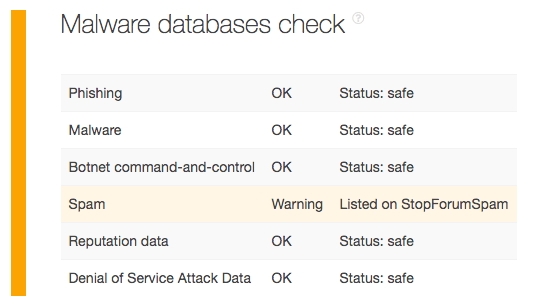
4. Prevents Spam from Reaching Users
TIP can also help users block spam, thus reducing the chances that recipients’ computers will get infected with malware. We ran the known spam-sending domain recreationalparksusa[.]info on it and found that it was on StopForumSpam. Further communication with anyone using the said domain should thus be blocked.
Apart from the four uses above, TIP also warns users against disreputable sites using data from Web of Trust: Safe Web Search & Browsing and other sources. It also flags IP addresses and domains that may be tied to DoS attacks using information from Open Threat Exchange (Alien Vault) and other sources.
---
Threat intelligence tools like TIP are a necessity for cybersecurity experts who want to make sure that their networks remain safe from all kinds of malware-based attackers. Proactive protection is critical if they wish to detect malware before these can do harm to their systems.
