White papers
Threat Hunting for Professionals:
The One-Stop Guide to Get Started
Are hackers getting smarter or is there something wrong with cybersecurity?
Here are a few hard truths. The losses caused by cybercrime continue to increase around the world — reaching billions of dollars’ worth of damage every year. Additionally, while businesses keep putting a lot of money into cybersecurity, there isn’t always a clear sign that investments are paying off.
Why is that? Well, one reason is that cybercriminals are constantly learning how to get around traditional defenses, and let’s face it, they are really good at it.
So how can individuals and organizations protect their confidential data? Is there anything that can be done to identify vulnerabilities before it’s too late?
Perhaps it’s time to reconsider conventional cybersecurity approaches, and here’s where a practice known as threat hunting comes in. When deployed correctly, it becomes a powerful weapon in the battle against cybercrime. Let’s find out how.
Table of contents
- The current landscape of threat hunting
- What is threat hunting?
- The threat hunting process
- Hunting modern threats with threat intelligence
- Best practices for a productive hunt
- Demo: Getting insights for the hunt
- 3 Real-word examples
- Concluding thoughts
The Current Landscape of Threat Hunting
The problem with many organizations today is that their stance towards threats is more reactive than proactive. For many, looking out for online dangers is a new thing to do. So when attacks occur, businesses are thrown off balance.
Threat hunting aims to put an end to reactive practices. Even though it’s a relatively new technique, it’s already starting to gain traction in various industries. In fact, one of the latest SANS Institute surveys shows that more than 40% of companies are already actively performing threat hunting operations.
However, the term still is quite unfamiliar to many and is surrounded by myths and misconceptions. So let’s take a closer look at how threat hunting emerged, what it is, and what it’s not.

What is Threat Hunting?
It’s hard to trace the origins of the practice back to a particular year, but it’s fair to conclude that it all started when experts began collaborating against nation-state attacks.
The term ‘threat hunting’, though, has a more specific history. It was first mentioned in 2011 in Information Security Magazine article entitled “Become a Hunter.” A memorable point in the article was that counter-threat operations are necessary to better fight back against cyber attacks.
The author further mentioned that companies would have to be active in hunting trespassers within their enterprise and highlighted two forms of intruders: external or persistent threats and internal actors that take advantage of their access privileges.
Common misconceptions of threat hunting
Before digging into the modern definition of the practice, it’s critical to dispel doubts and debunk some popular myths.
1. Threat hunting is a reactive approach and is similar to incident response.
Not quite true. On the contrary, it is about taking charge of a company’s defenses and being proactive throughout the process. Threat hunting professionals think ahead and assume that dangerous elements can always get past even the sturdiest of IT fortifications and that the infrastructure can be breached without any alerts sent. Hunters create hypotheses based on threat intelligence analysis and act on them to figure out where possible trespassers may be lurking.
2. Threat hunting can be fully automated.
This is far from the truth since the activity itself requires the intelligence of human analysts and investigations to be based on hypotheses. One of the main purposes of threat hunting is actually to identify the aspects that may have been overlooked by automated reactive systems.
3. Threat hunting efforts can’t be measured.
That isn’t correct either. There are a few criteria that can be measured, such as the number of dangerous instances identified and the reduction of dwell time thanks to early detection. The maturity of the team can also be estimated in a way — e.g., by viewing the number of unique hypotheses, data sources used, completed hunts, unique hypotheses tested, and findings reported.
Internal vs. external threat hunting
The practice can either be outsourced or applied as an internal program. But in order to decide which one would work best in each individual case, it’s important to learn about the advantages and disadvantages of these two approaches.
| Pros | Cons | |
|---|---|---|
| Internal threat hunting: Deploying in-house teams and protocols to proactively spot network vulnerabilities and threats |
|
|
| External threat hunting: Outsourcing the practice to a service provider |
|
|
The definition of threat hunting
With all of the above in mind, we see threat hunting as...
“The practice of proactively searching and identifying cyber threats at the earliest possible phase of an attack. It involves leveraging threat intelligence to identify gaps within and outside enterprise perimeters, as well as following analytical practices and implementing the right security tools.”
Five Steps of Threat Hunting
Now that you’ve got an idea of what threat hunting is all about, let’s take a closer look at how it works in practice. It’s important to remember that threat hunting is not a one-off initiative but a multi-stage, continuous process which can be broken down into several steps. Let’s examine them one by one.
| Step 1 | Step 2 | Step 3 | Step 4 | Step 5 |
|---|---|---|---|---|
| Hunt preparation | Hypothesis | Pattern validation | Immediate actions | Knowledge sharing |
1. Prepare for hunting
The team assigned to perform the task gets equipped with the proper threat intelligence data and information about the current organization’s environment including its policies, guidelines, data about previous incidents, and the like.
2. Generate hypothesis
Once preparation is complete, the next step is the generation of hypotheses. What systems or accounts are the most likely to be targeted? What could be the attackers’ techniques and their corresponding probability of happening? Decisions can then be made regarding the instruments or tools required to verify these hypotheses.
3. Validate hypotheses and uncover patterns
At this stage, teams find out about the latent threats connected to hypotheses. This means that some hypotheses at this point have already been discarded while others are being prioritized. After an attack has been identified, the next step is to reconstruct it and find new tactics and patterns that were used to make it happen.
4. Acting upon discoveries
Once a breach or vulnerability is detected, it’s important to take immediate action. This may take different forms depending on what has been found. For instance, if the vulnerability is spotted in the infrastructure, threat hunters should contact a security team to patch and resolve it. In the event of a breach, an incident response team should take charge and respond.
5. Enrich systems and disseminate knowledge
The final step in threat hunting is making all data regarding the vulnerabilities, threats, and patterns available to the rest of the organization. The rationale for this is to share the knowledge on how to counteract threats and keep the company’s network defenses moving forward.
Hunting Modern Threats with Threat Intelligence
Finding cyber threats is no simple feat. The good news is that aspiring threat hunting teams can perform threat intelligence analysis to learn about the current threat landscape and, therefore, come up with better hypotheses. Below are some examples of the modern dangers that threat intelligence is able to detect.
Impersonation
This type of attack is a malicious practice where the perpetrator assumes the identity of a third party — a business entity, a supplier, or even an employee. Impersonation takes various forms from website forgery to business email compromise (BEC) scams.
The threat could seriously harm business reputation and cause substantial financial losses. In 2018, damages from BEC reached $12.5 billion, according to the FBI’s latest public service announcement. Let’s take a look at some ways threat intelligence analysis can help detect such attempts.
| Actions | Parameters to examine |
|---|---|
| Carry out SSL configuration analysis |
|
| Evaluate WHOIS records |
|
Man in the middle
A man-in-the-middle attack occurs when hackers secretly intercept communication amongst two parties to obtain confidential information. A notable example of this was when cybercriminals swindled more than £300,000 out of a British couple during their property sale. The act involved perpetrators hacking into the owner’s email, impersonating the owner, and informing the financial institution to send money to a different account.
| Actions | Parameters to examine |
|---|---|
| Analyze SSL configurations |
|
Phishing
In its basic form, phishing is the act of sending fraudulent communications whose sources seem reputable but are intended to deceive its recipients. It is the most common method for hackers to get confidential or sensitive information. In fact, phishing is used in more than 70% of cases by attacking groups according to Symantec.
| Actions | Parameters to examine |
|---|---|
| Conduct infrastructure analysis |
|
| Inspect WHOIS data |
|
| Inspect mail servers |
|
Malware
Malicious software, or simply malware, is a term that describes software or code that is intended to harm computer systems. These programs are capable of stealing sensitive information, deleting important files, or even causing systems to stop working entirely. Based on a study by AV-TEST Institute, the numbers of new malware detected have doubled between 2018 and 2017.
| Actions | Parameters to examine |
|---|---|
| Examine infrastructure |
|
| Scan websites for potentially dangerous files |
|
| Double-check malware databases |
|
| Scrutinize malware scores |
|

Best Practices for a Productive Hunt
Now that you are aware of these modern threats, let’s move on to the best practices in threat hunting. So how do you get the most of it?
Know your environment – A prerequisite to spotting abnormal activities in your system is an understanding of its normal operational activities. It’s essential that threat hunters spend a good amount of time examining the whole architecture of their organization.
Think like a hacker – A professional threat hunter must be able to step into the shoes of an attacker in order to anticipate his next moves. More specifically, a good specialist will profile different types of hackers, emulate their motivations, analyze what assets these criminal might be after, and what tactics they are likely to deploy.
Use quality data and resources – Leveraging data from a wide range of sources is important to keep visibility throughout the threat hunting process. This helps hunters comprehend their operational environment and quantify vulnerabilities to prepare plans to counteract incoming threats.
Ensure endpoint security – Threat hunters have to monitor network devices and other endpoints to safeguard their security perimeters and keep control over all activities, authorizations, and software used in the company. Negligence in any area could lead to gaps cybercriminals can exploit elsewhere.
Interact with colleagues and IT personnel – Considering the human factor is crucial to the overall success of the practice. This means threat hunting specialists should collaborate closely with their IT staff not only when incidents occur, but on a regular basis to understand how systems operate and detect their most exploitable weaknesses.
Keep up with the cyber landscape – Threat actors are always looking for new ways to perform attacks and abuse security systems. Keeping up with them requires threat hunters to stay forearmed with up-to-date threat intelligence so they won’t be left behind.
Do not let your guard down – On top of it all, stay alert to signs of suspicious activities, remembering that cybercriminals are getting more creative with their attacks.
Demo: Getting Insights for the Hunt
As part of threat hunting activities, teams need comprehensive data to make sense of the cybersecurity landscape. For that purpose, threat intelligence reports can provide hunters with a wide range of information on risks and threats and help red-flag suspicious items for further investigation.
To get a deeper understanding of the topic, here are several ways how Threat Intelligence Platform can enrich threat hunting practices today.
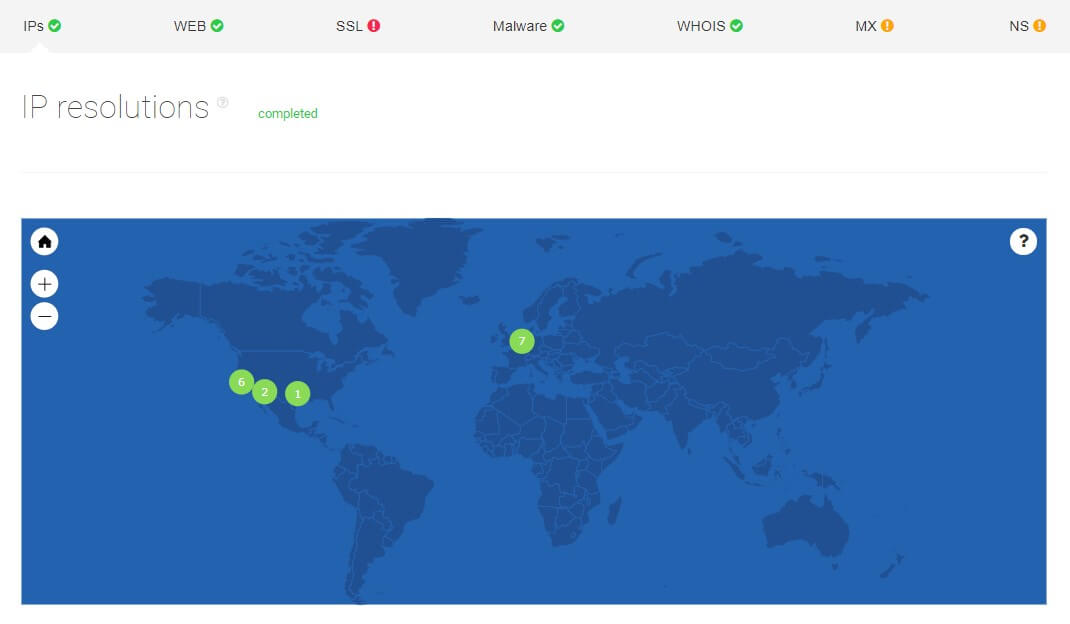
Inspecting a domain’s locations
A threat intelligence analysis report lets you see the graphical distribution of IPs to confirm their locations. For example, imagine that a distributor is looking to sign a deal with a manufacturer. Say, a pharmaceutical company claims to be exclusively operating in one country, but the prospective partner just wants to make sure.
After the analysis was made on its networks, it turns out that the manufacturer also has IP addresses in another location. An assigned threat hunter can look further into that and investigate the reason why.
Examining domains connected to a target website
A popular tactic used by hackers is to set up a group of websites under a single IP address. If a threat hunter identifies one as risky, it’s particularly important to do proper research and see whether it’s part of a bigger cluster of dangerous domains.
Let’s say a threat hunter named John has identified a suspicious website. He can use a threat intelligence platform to perform a detailed analysis of the target and see what other domains are connected to it.
Once he has received a report of all related websites, John can send it off to his cybersecurity specialists who can then input the data into the company’s cyberdefense system – flagging all marked domains as risky to visit or interact with.
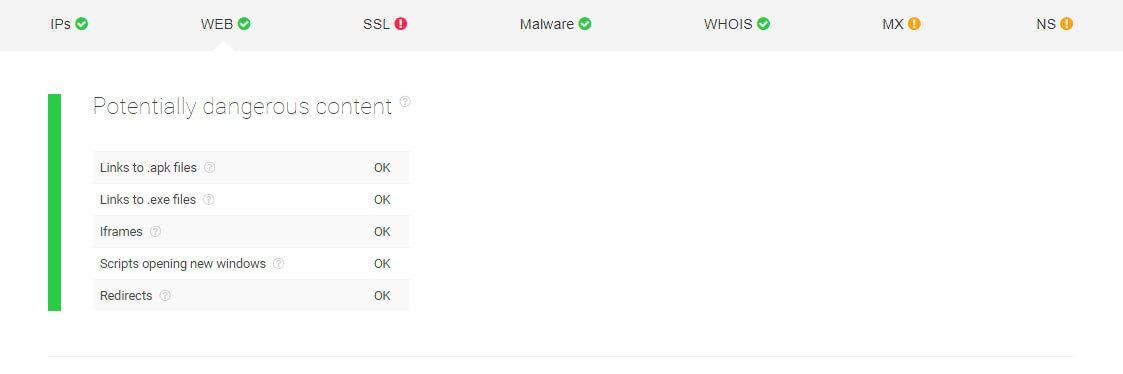
Recognizing potentially dangerous content
Another way a threat hunter can understand the threat landscape is by examining websites for potentially dangerous content.
Threat hunter Jane, for instance, wants to make sure that the websites her workmates frequently visit do not contain malware. She uses an analysis tool to check .apk files or programs that can run malicious codes, .exe files or software that can install unwanted applications on systems, or iframes which could be used to inject undesirable scripts.
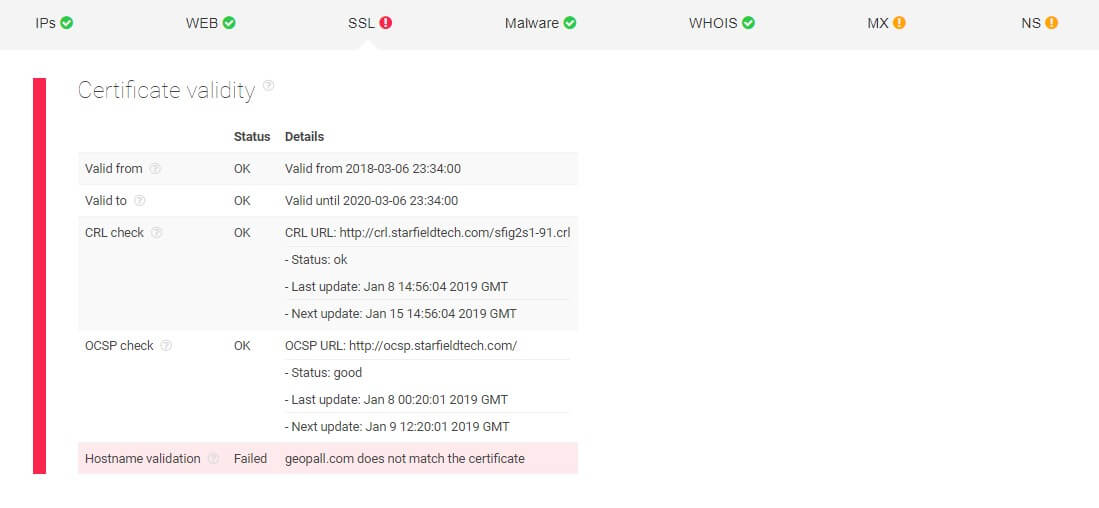
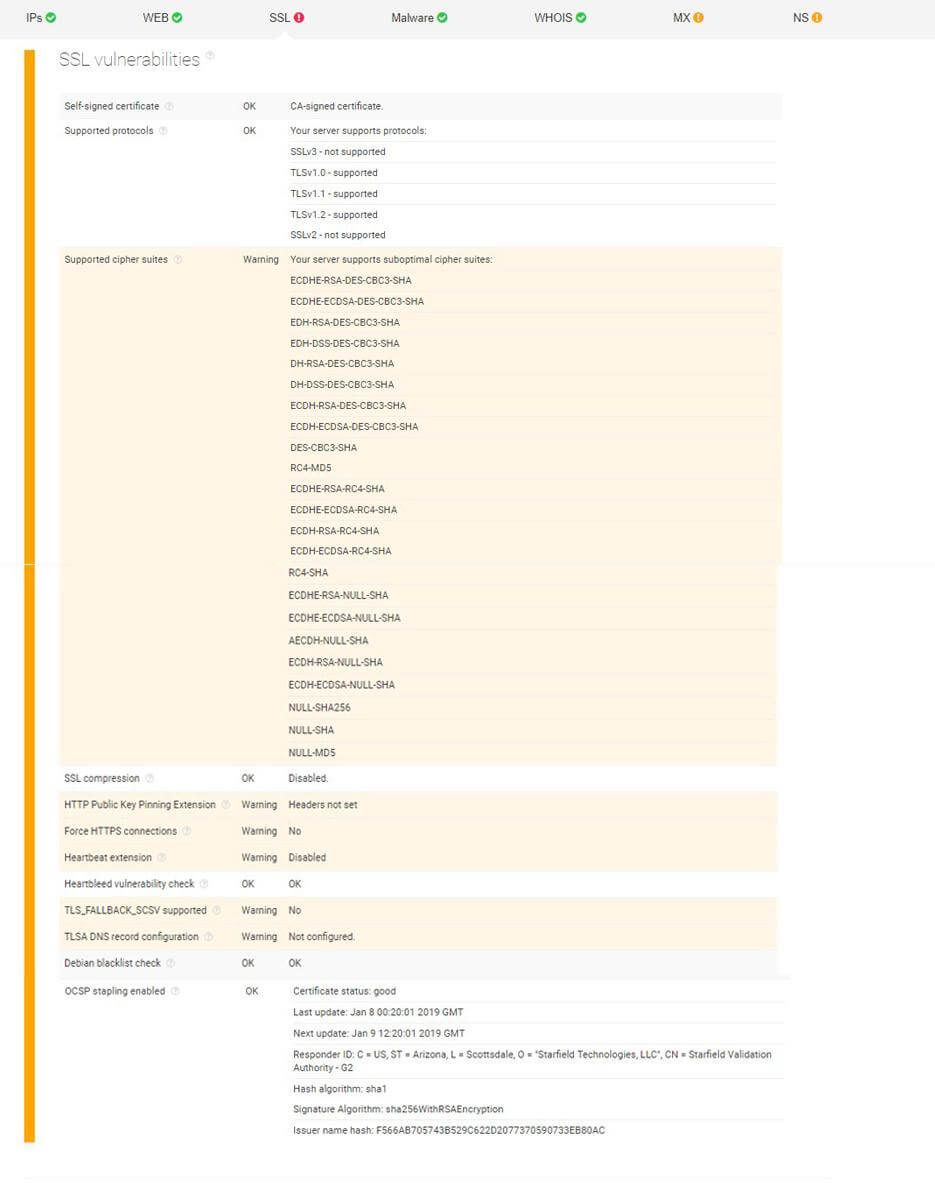
Checking for SSL vulnerabilities
Jim needs to share critical information about his company to a third party, but he is unsure if that party’s site can be trusted. He employs a threat hunting team which performs an SSL configuration analysis on the target before proceeding.
The team comes back with a report which shows several warnings. For instance, both the site’s hostname validation and TLS_FALLBACK_SCSV are flagged red. This means that there is some discrepancy in the validity of the target’s security certificate and that the website is not secure from POODLE attacks — making it susceptible to impersonation.
He also notices that the heartbeat extension under SSL vulnerabilities is not enabled, opening up the possibility of a Heartbleed bug entering the network and stealing sensitive data.
This information makes Jim postpone the decision to work with the third party as it appears to have several exploitable gaps that can result in a data breach.
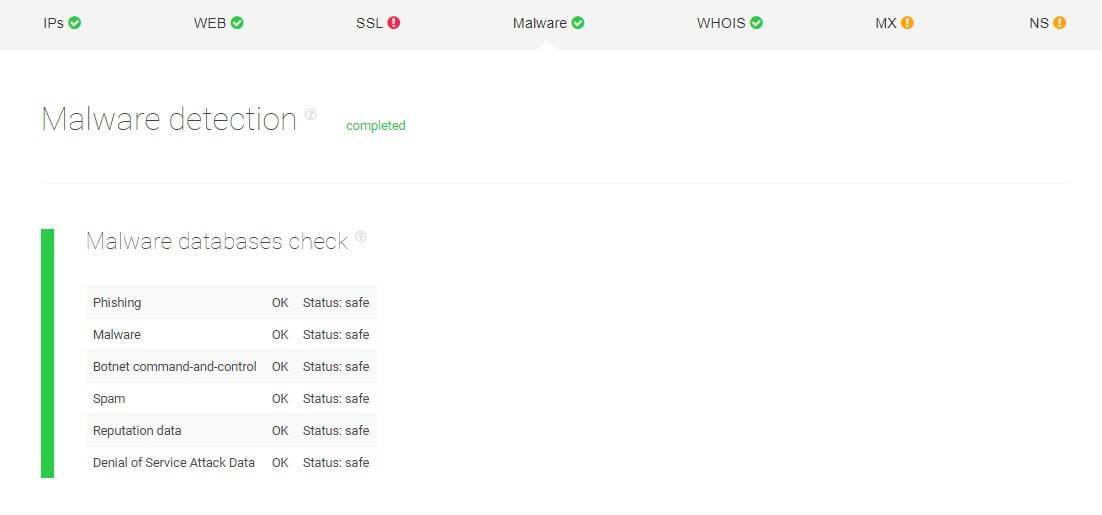
Looking into malware databases
When threat hunters are performing threat intelligence, some processes can be automated to make things simpler. Consider, for instance, threat hunter Mike who has a hypothesis regarding a suspicious website.
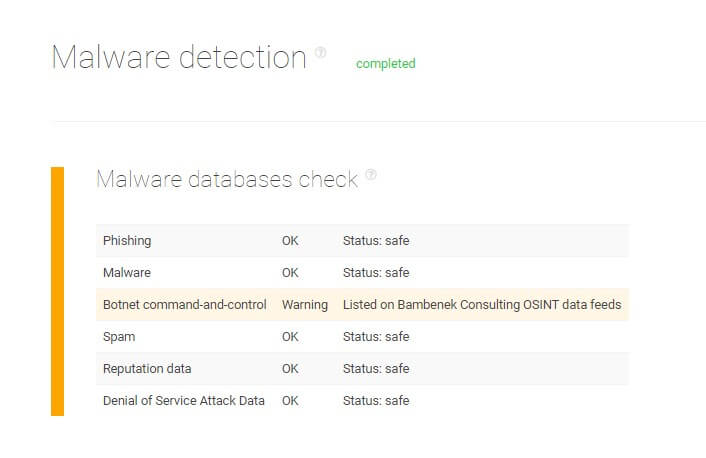
To confirm or disprove this hypothesis and make sure his company’s network doesn’t get infected, he runs the website through a malware detection process that automatically checks malware data feeds across the Web. The returned report will inform him whether the target domain is considered risky or safe.
As seen below, the analysis results came back all green, which means the website Mike had suspicions on doesn’t contain malicious software.
Deep insights from WHOIS records
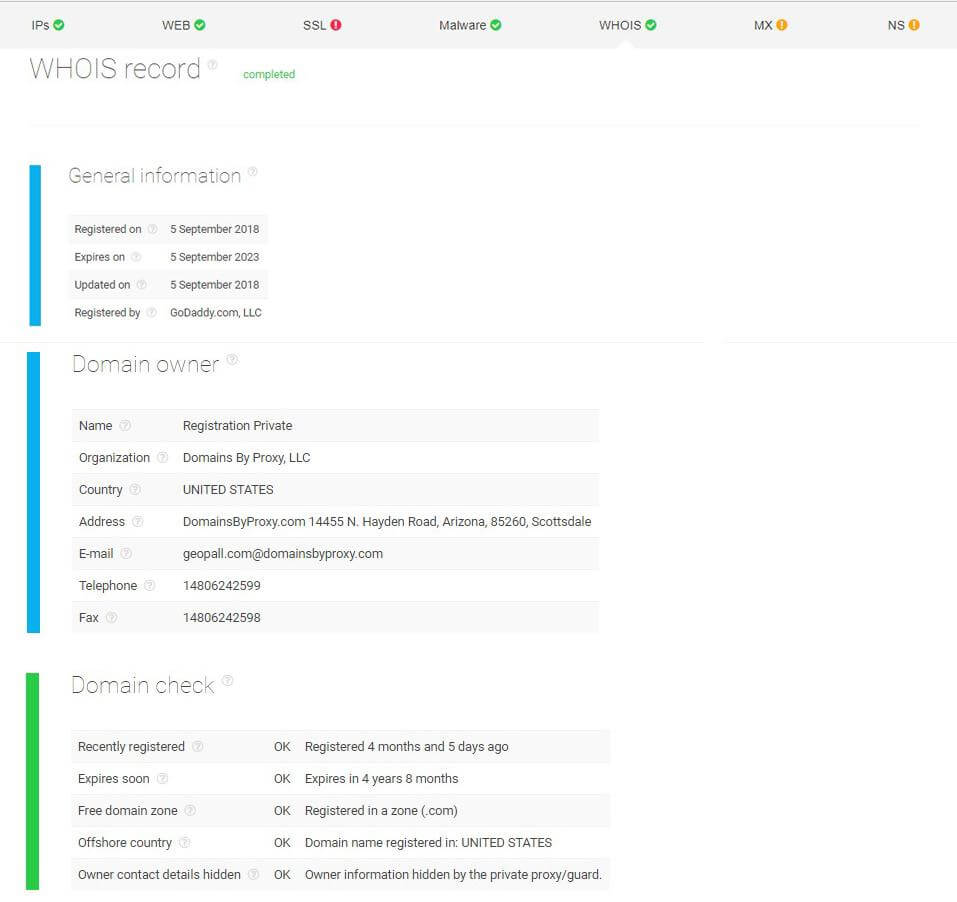
Leveraging WHOIS data is another way for threat hunters to gain some knowledge about an online entity. Since domain records contain a number of critical details such as domain registry information, owner’s contact details, location and more, which could be crucial in detecting suspicious activities.
Let’s say, Phillip, a business owner, plans to transact with a financial agency claiming to have been in the industry for 10 years. He asks someone in his team with threat hunting experience to look into the case. The hunter then performs threat intelligence analysis and inspects the WHOIS data feed of the report.
Upon reviewing the domain record, it turns out that the company has only been around for a few months and that the domain owner’s contact details are not consistent with what is indicated on the agency’s website — possibly meaning that the company hasn’t been totally honest with Phillip who is now having second thoughts about its identity and credibility.
Performing internal infrastructure analysis
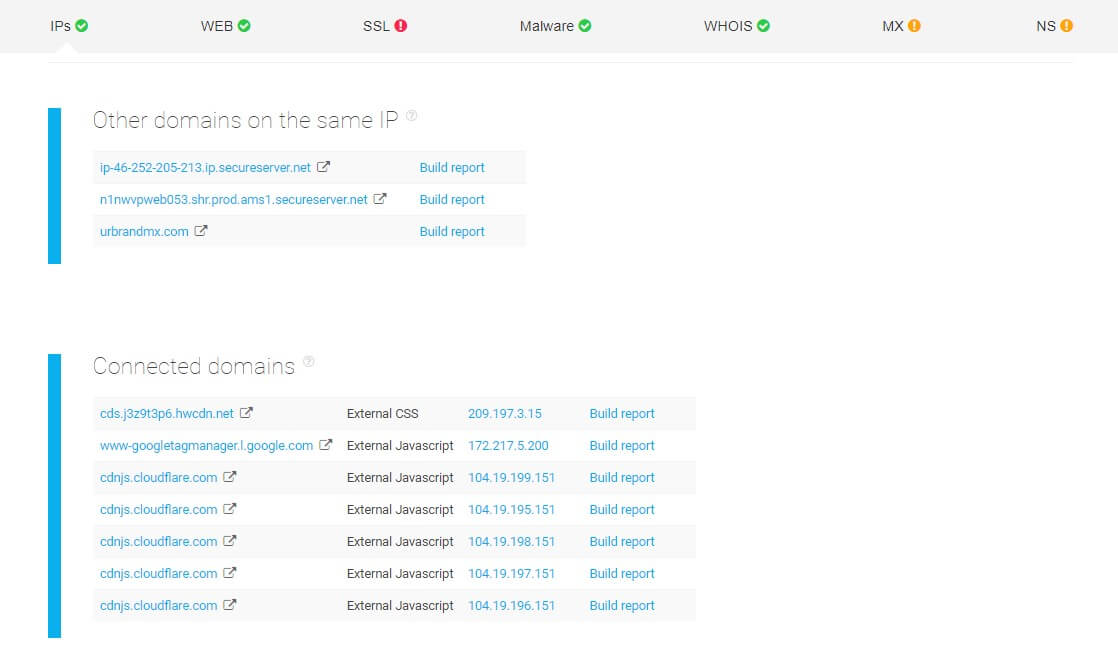
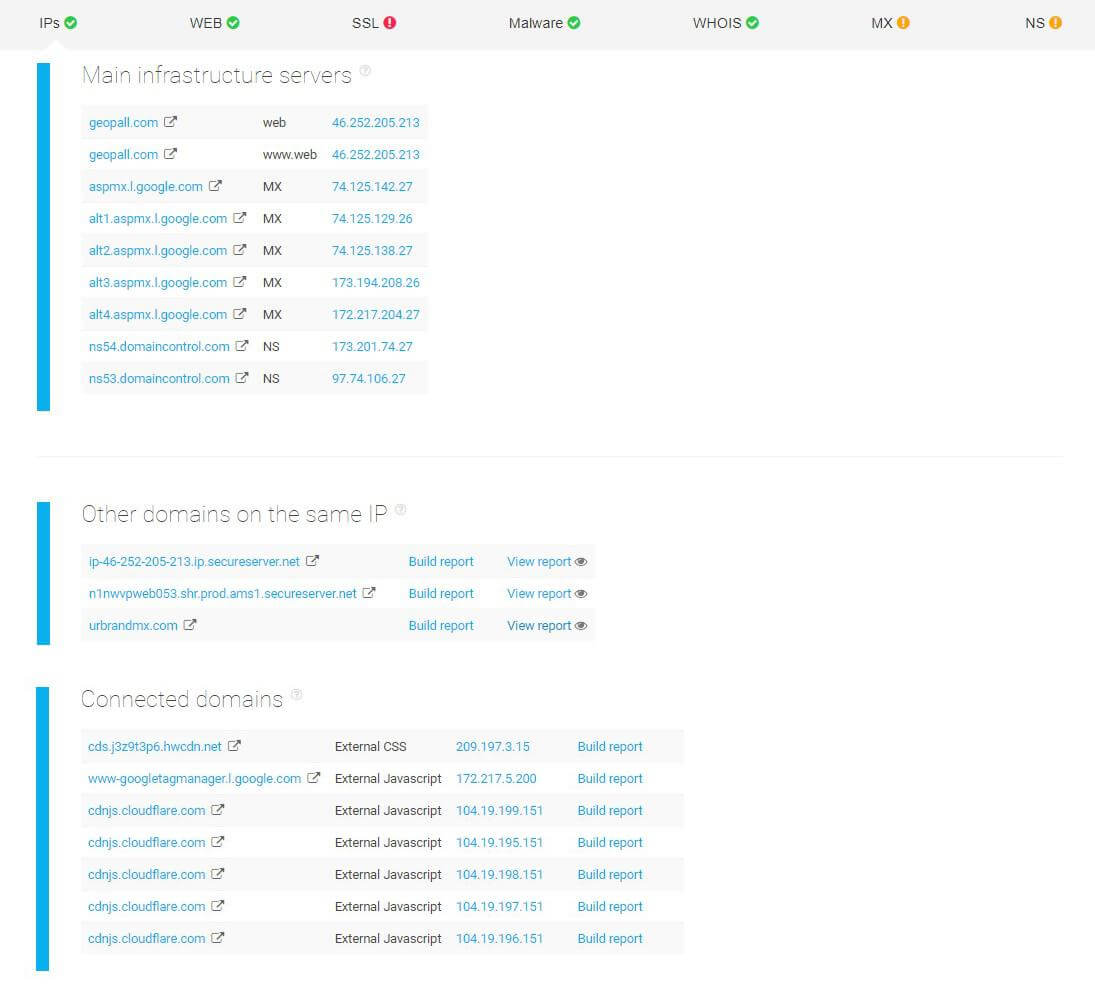
Karen, a newly-hired company engineer, is assigned to do a thorough check of her organization’s infrastructure to detect any present vulnerabilities in their website configurations.
She starts by performing an infrastructure and malware analysis — looking at connected domains, notably on the same IP. The first two domains on the same IP don’t have any major red flags. However, the urbrandmx.com domain is blacklisted and may potentially contain malware.
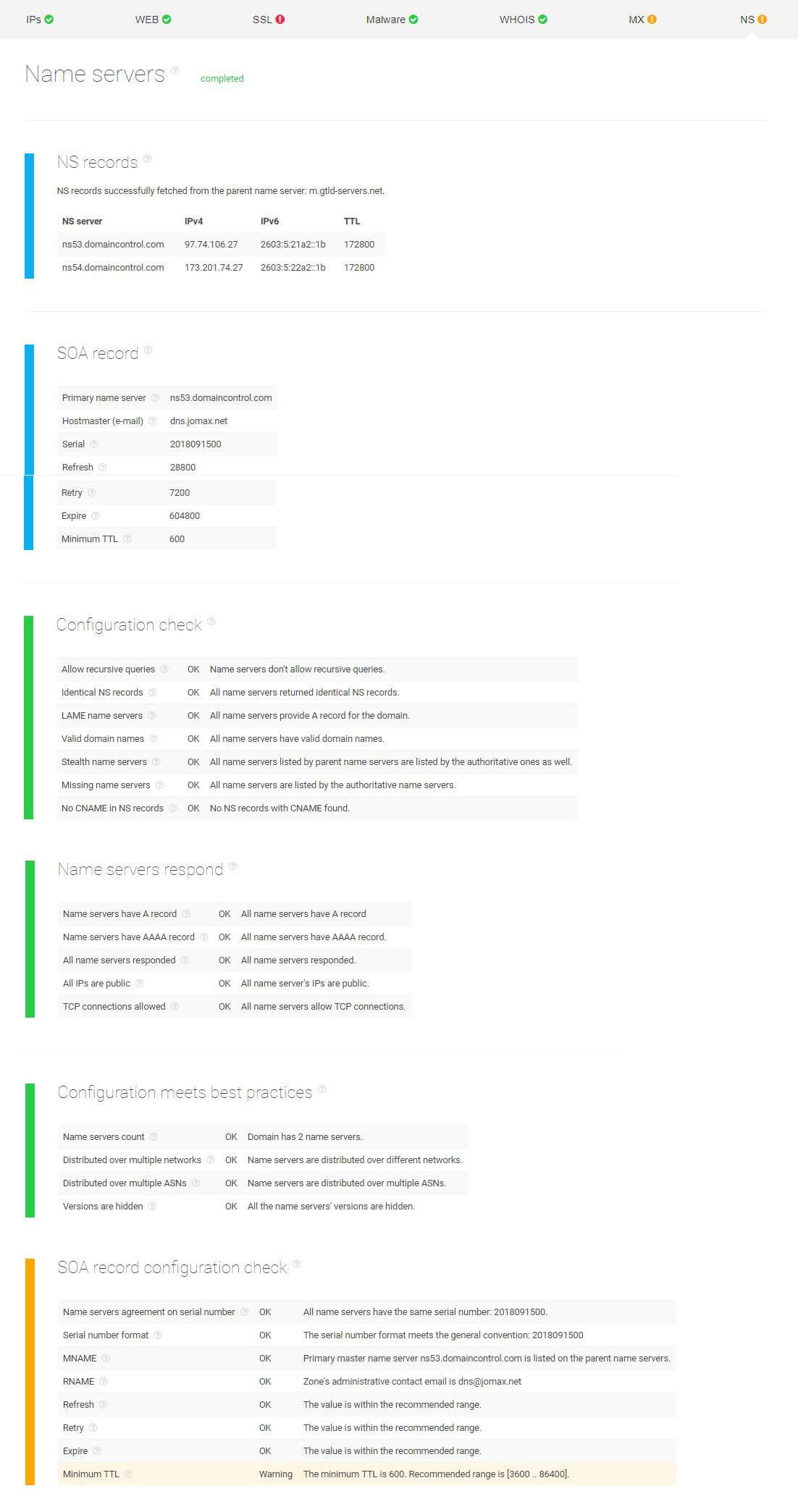
Particular attention is paid to the company’s mail servers. The report below shows that Karen’s company doesn’t have DMARC (Domain-based Message Authentication, Reporting, and Conformance) configured. This is particularly important as this validation system is designed to detect and stop email spoofing. Apart from that, Karen is also notified that their mail settings aren’t up to Google’s standards. The good news is that their mail servers aren’t blacklisted anywhere and name servers return identical MX records.
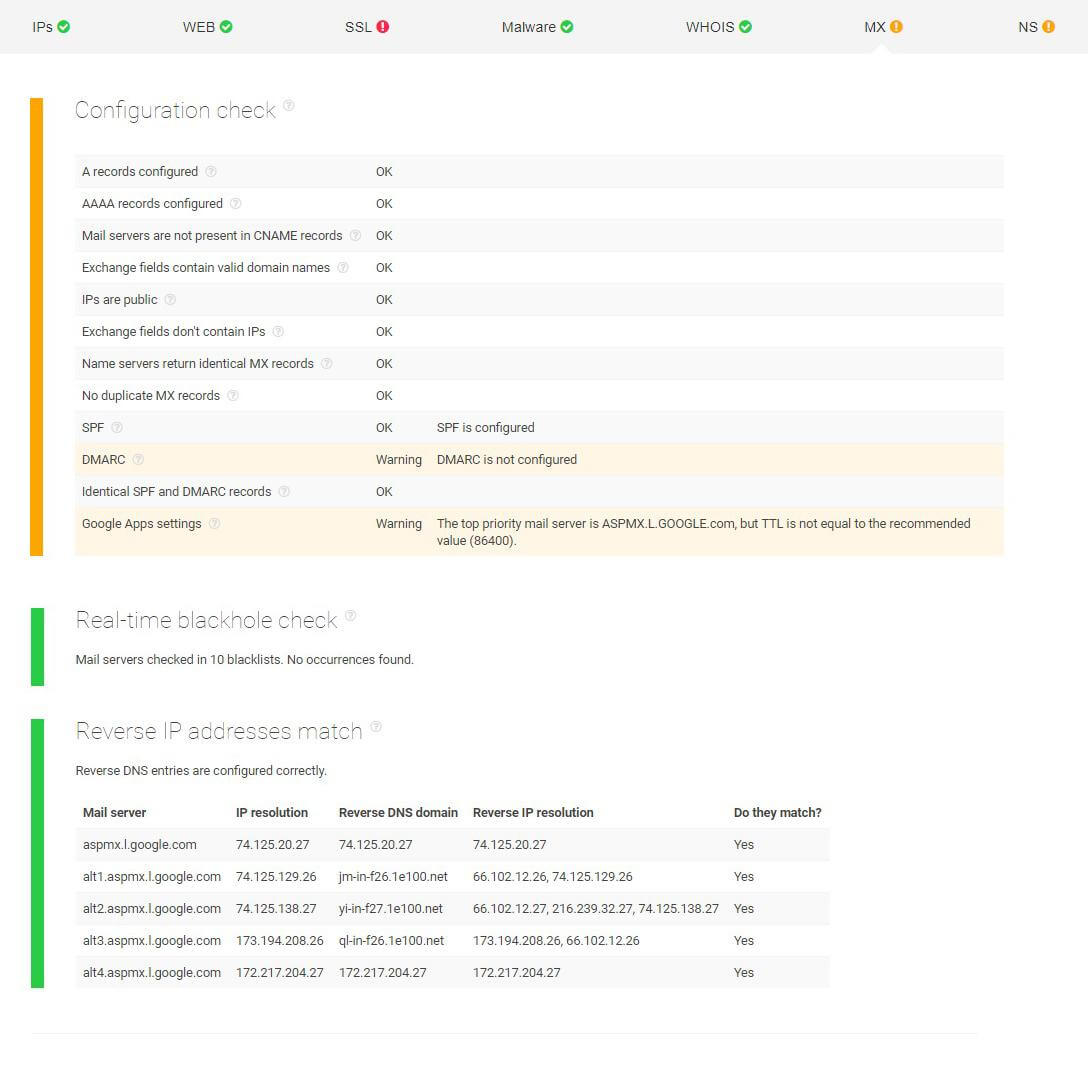
Next, Karen looks into the name servers. Among other parameters, she checks the name servers’ location and inspects stealth name servers since misconfigurations here might result in unpredictable behavior. As seen from the screenshot below, her company’s name servers successfully passed the configuration check and, for now, they appear safe for use.
The only parameter that is not up to the recommended standards is the Minimum TTL (time-to-live) whose value is not within the recommended range. TTL is an essential setting in every DNS record that indicates how long a record has been cached by a DNS server.
3 Real-World Examples
In this section, let’s take a closer look at a few known malicious domains to illustrate what red flags and warnings a threat intelligence analysis can unveil.
#1 Malware detected
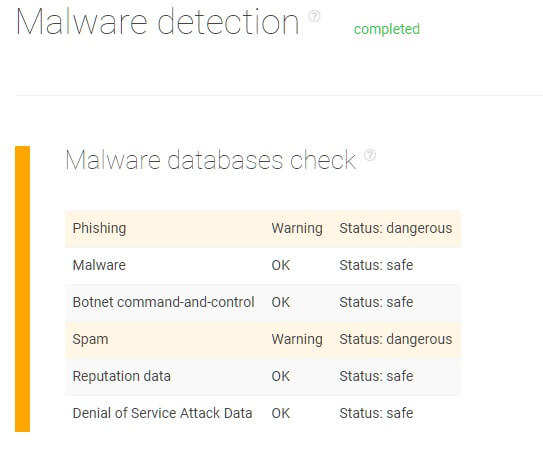
In 2018, 2SPYWARE, a portal providing cybersecurity news, warned their readers about mail.ru being a potentially dangerous page containing the virus Go.mail.ru. Once downloaded, the virus would operate as a browser hijacker — notably aiming Google Chrome and Mozilla Firefox — and redirect users to unintended web pages and search results.
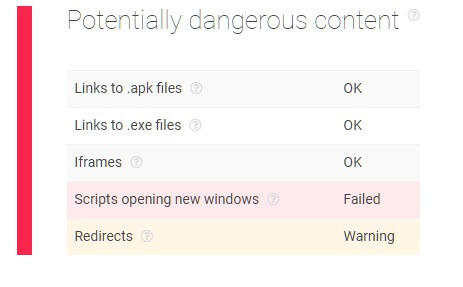
As seen in the screenshots below, the website is flagged as containing phishing and spam content as well as redirects potentially leading to malicious websites. What’s more, the page appears to have scripts attempting to open up new windows without users’ consent.
#2 High-risk SSL certificates
In January 2019, ethereumcv.io and etcv-wallet.com were flagged as scam sites after a victim shared his negative experience on Reddit. At first sight, ethereumcv.io looked legitimate and even had a roadmap and a white paper.
Upon browsing, however, the page redirected the visitor to his online wallet, prompting him to claim 3 ETVC coins in exchange for 1 ETH. It was during that procedure that private keys were stolen — permitting the theft of 131 ETH coins.
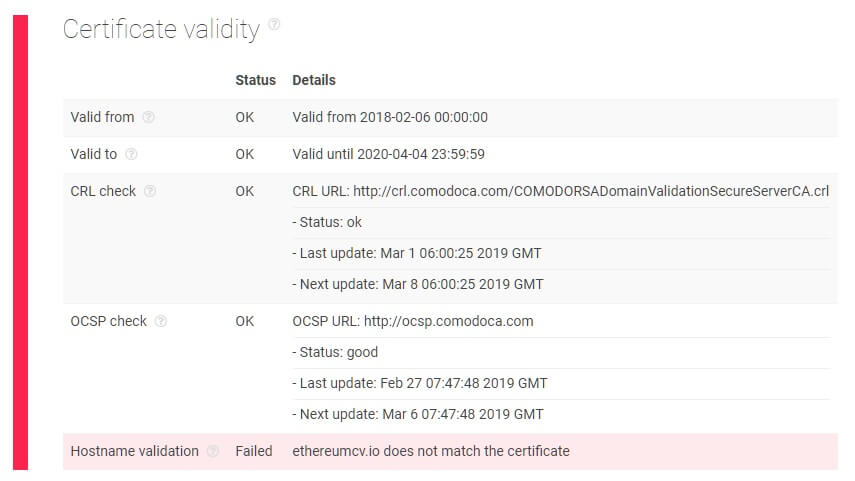
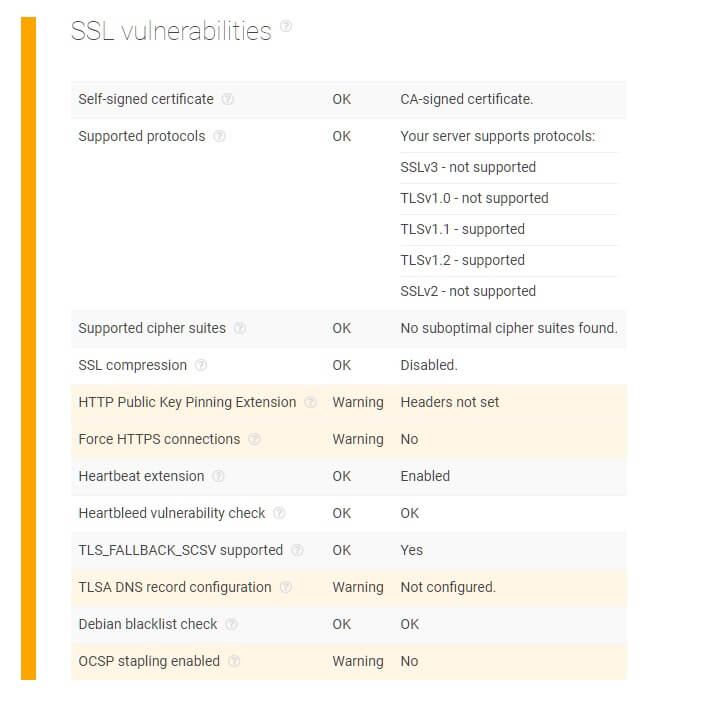
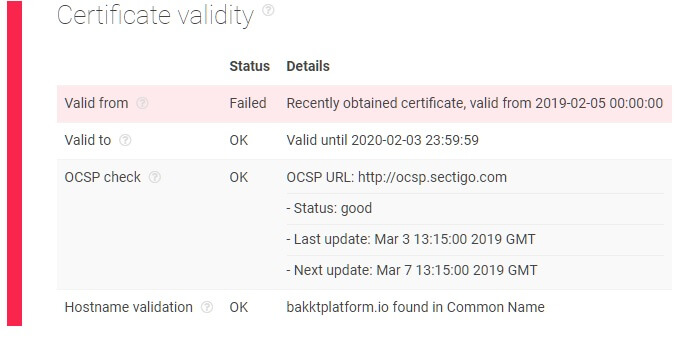
Running the domains through a threat intelligence analysis, both corresponding websites failed to validate their SSL certificate and revealed other vulnerabilities including headers not set for HTTP public key pinning extension, non-enforced HTTPS connections, a non-configured TLSA DNS record, and non-enabled OCSP stapling.
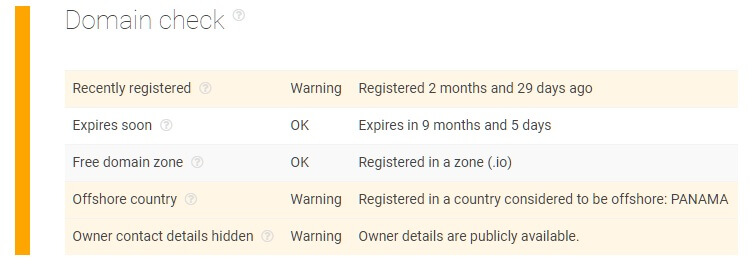
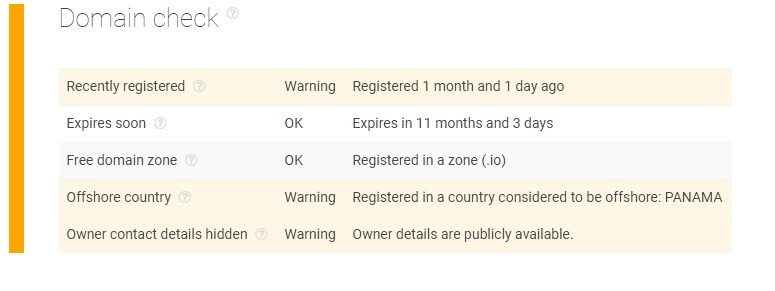
Furthermore, the “domain check” portion of the report also reveals that both sites are newly-registered with their location of registry identified in Panama and contact details hidden — all of which are potential signs of malicious activities.
#3 Impersonation signs
Unfortunately, fake websites are common nowadays, misleading customers and negatively impacting brand reputation. This is what happened to bakkt.com, a blockchain-based fintech platform, whose website was forged under the domain name bakktplatform.io — where a fake launch date was announced with the goal of tricking users into sending Bitcoin by promising attractive returns.
Though the website seemed convincing, there were some initial signs of the offer being a scam including strange statements and typos. Running bakktplatform.io through a threat intelligence analysis instantly showed concerning points.
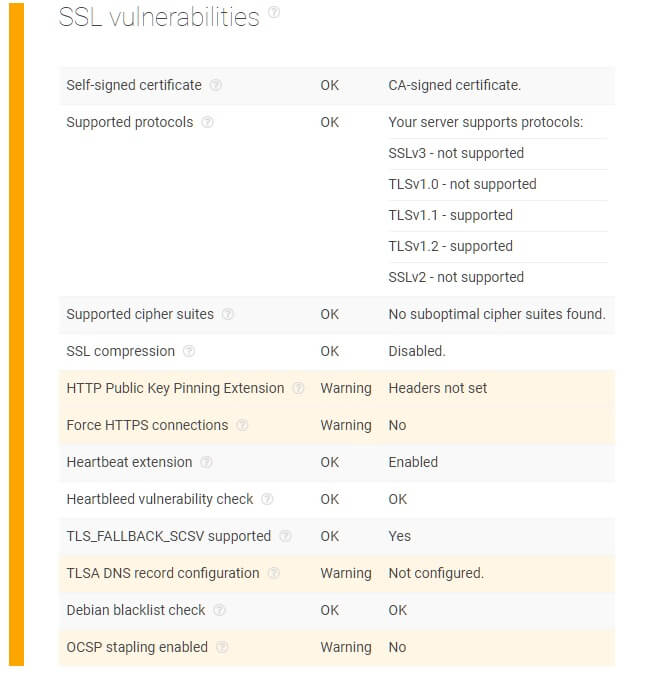
For instance, there were issues with SSL certificates — i.e., host's response not containing HPKP headers and potentially leading to impersonation as well as a non-configured TLSA DNS record and non-supported OCSP stapling.
Moreover, upon checking the report under WHOIS, warnings indicate that the registration is recent and it has been performed in an offshore country.
Concluding Thoughts
Threat intelligence provides numerous advantages to companies that take a proactive stance in their cybersecurity and leverage threat hunting practices.
Yet in order to make the best out of it, decision-makers should remember that efficient threat hunting always starts with a reliable source of threat intelligence. It’s a continuous process that takes time and dedication before teams start seeing positive results in their activities.
As a company owner or a decision-making employee, it’s vital to reinforce your organization’s cybersecurity systems against the ever-growing threats on the Internet. If you’d like to know how Threat Intelligence Platform can help, contact us today at service.desk@threatintelligenceplatform.com.
Read the other articlesTo download the full article in PDF, please fill in the form.
Have questions?
We work hard to improve our services for you. As part of that, we welcome your feedback, questions and suggestions. Please let us know your thoughts and feelings, and any way in which you think we can improve our product.
For a quick response, please select the request type that best suits your needs.
Threat Intelligence Platform uses cookies to provide you with the best user experience on our website. They also help us understand how our site is being used. Find out more here. By continuing to use our site you consent to the use of cookies.