White papers
Threat Intelligence API: Walking the Cybersecurity Talk

To many, threat intelligence still sounds like a strange term. Some specialists even claim that it’s not for every business out there and recommend either adopting it correctly or abstaining altogether… and they might have a point.
The truth is that failing to deploy threat intelligence the right way is like painting with a broad brush with no idea of the bigger picture. Adding to this is the fact that making informed decisions in the world of cybersecurity requires you to have the necessary data close at hand.
The good news is that software such as Threat Intelligence API allows actionable data to be readily integrated into various processes and solutions. This product is composed of six sub-APIs: Domain’s Infrastructure Analysis, SSL Certificate Chain, SSL Configuration Analysis, Domain Malware Check, Connected Domains, and Domain Reputation. Each of them provides specifics on specific areas of the host’s infrastructure.
But before we talk about them in more detail, let’s start with the current threat landscape to understand the relevance of threat intelligence in general and Threat Intelligence APIs in particular.
Table of contents
- The Threat Landscape Today
- Understanding What Threat Intelligence Is and Is not
- Types and Sources of Threat Intelligence
- Leveraging Threat Intelligence APIs: The Whos and The Hows
- What Threat Intelligence APIs are Available Today
- Concluding thoughts
The Threat Landscape Today
Organizations are so reliant on the Web these days that cybercriminals find it very profitable to exploit such connectivity to disrupt daily operations and steal funds. But it’s not just the money that the hackers are after. Sensitive data can turn equally beneficial or even more so.
What’s more, perpetrators tend to succeed despite beefed-up organizations’ cyber defenses in place — costing companies millions of dollars on average per data breach.
This is probably why the adoption of proactive cybersecurity approaches like threat intelligence has been continuously increasing in the past few years. A 2018 SANS survey, for instance, reveals that 81% of their respondents found threat intelligence helpful. It also mentions that more than 70% of respondents claimed they had better insights into various threats and attacks compared to the past, thanks to threat intelligence.
Experts in cybersecurity view these statistics as indications that threat intelligence will continue to be applied in future organizational operations. However, in order to get the most out of it, companies will need to have a clear understanding of what the practice will and won’t allow them to achieve.
Understanding What Threat Intelligence Is and Isn’t
To put it simply, threat intelligence is the knowledge acquired by collecting and analyzing information on online threats. It can be obtained through numerous sources such as data feeds, cybersecurity communities, domain details, Internet service providers, geolocation data, and more.
Technological advances have allowed threat intelligence to be incorporated into software — which is the case with Threat Intelligence APIs that can provide more in-depth insights into threats. For example, a domain malware check API can perform a background check on a website to see if it is flagged in known malware databases.
As the years go by, threat intelligence is becoming more and more widespread. But even if that’s the case, there are still several things that many users find unclear about it. To eliminate these doubts, here are four common misconceptions about threat intelligence and the reality about them.
- Threat intelligence is only for big companies
On the contrary, threat intelligence allows facilitating some cybersecurity tasks that small businesses might not have enough manpower to accomplish. For example, instead of hiring expensive specialists to verify the trustworthiness of numerous web pages, a company interacts with, one of the Threat Intelligence APIs can be used to automatically calculate a domain’s safety score. - Threat intelligence is only for cybersecurity teams
As hackers usually look for the line of least resistance, one of their common techniques is to target businesses through the employees with very little knowledge about cybersecurity. This is why threat intelligence should be disseminated across the whole organization, something that can be done in a scalable fashion through APIs. For instance, employees across departments can leverage such software to verify if the websites they interact with contain malware or are considered dangerous. - Cybersecurity solution providers can do without threat intelligence
Conversely, threat intelligence obtained through APIs can enrich the data gathered via other means, which ultimately allows cybersecurity enterprises to offer higher quality solutions by providing more precise and actionable intelligence.
Types and Sources of Threat Intelligence
Certainly, threat intelligence is not created from thin air. As mentioned earlier, it can be acquired through several means and then integrated into customers’ systems through APIs. Let’s take a closer look at some of them.
Signals intelligence (SIGINT)
This form of threat intelligence is collected via information coming from the intercepted signals of a target such as their communications and electronics. SIGINT relies on capturing external raw data which may come in the form of monitoring incoming and outgoing data packets in a network.
One example of this is domain’s infrastructure analysis API, which queries servers and subdomains to provide customers with the website’s latest infrastructure data. Information that can be retrieved here includes details on domain’s geolocation, sub-network, and more.
Geospatial intelligence (GEOINT)
Geospatial intelligence works by taking advantage of imagery and geospatial information to evaluate human activities around the world. Modern technology and infrastructure allow users to take GEOINT a step further.
Using an IP geolocation API, for example, can let cybersecurity teams detect unauthorized access to networks, providing hints on where the attack is coming from. This can be acquired through details obtained from IP addresses, which apart from the location also include data on the time zone, partial ownership information, Internet Service Providers, and more. Domain's Infrastructure Analysis API, which is part of Threat Intelligence API, can also reveal web servers’ geolocation information, subdomains' servers, mail, and name servers.
Threat intelligence feeds
These feeds are streams of data that can be obtained as indicator feeds, paid feeds, strategic partnerships, bulletins, and internal intelligence gathering. Individual feeds often focus on providing details on a single area of interest, including:
- Suspicious domains
- Code found on pastebins
- Collection of known malware hashes
- IP addresses flagged with malicious activity
- ... and more
The primary advantage of a threat feed is that it provides users with knowledge of potential threats that they weren’t aware of initially. When chosen carefully, the right feed can provide visibility even on unknown threats. It can also be used to fill knowledge gaps regarding existing malware.
Threat Intelligence APIs that were mentioned earlier — SSL Certificate Chain, Connected Domains, and Domain Reputation Scoring, among others — all collect intelligence from data feeds. They can be used to analyze the domain infrastructure behind hosts and help spot various threats such as known C&C servers tied to malware, URLs associated with phishing or typosquatting, and other dangerous indicators.
Leveraging Threat Intelligence APIs: The Who’s and the How’s
It would certainly be a mistake to think threat intelligence is only useful for corporations or solely for cybersecurity specialists. In fact, cybersecurity departments, security enterprises as well as various personas from both SMEs and large companies can put Threat Intelligence APIs to good use. Here’s what they can do:
- Chief Information Security Officer (CISO) – APIs providing threat intelligence data can contribute to CISO decision-making by offering real-time insights into external threats and, therefore, helping them identify the most pressing vulnerabilities, which subsequently enables the efficient allocation of cybersecurity resources.
- Chief Executive Officer (CEO) – combining intelligence gathered through Threat Intelligence APIs allows CEOs, on behalf of their companies, to provide clients seeking data enrichment solutions with high-quality and precise cybersecurity data.
- Threat analysts – with Threat Intelligence APIs, analysts can integrate obtained threat data with their cybersecurity tools to optimize workflows and enrich the intelligence gathered from other sources which would make them more effective in their roles.
- Incident responders – accurate information on current and potential threats integrated into systems via Threat Intelligence APIs can be crucial for response teams as it enables them to make informed decisions immediately during incidents. Aside from that, it also improves the remediation efforts when filling in security gaps in the company network.
What makes Threat Intelligence APIs even more special is that they allow integrating actionable intel directly with existing tools for better results. Let’s take a look.
Threat Intelligence APIs Available Today
Threat Intelligence Platform’s solution called Threat Intelligence API is a collection of individual APIs that allow users to acquire specific details regarding a particular domain. Each of its components can be used exclusively or with one another.
You can even think of these APIs as building blocks and the Threat Intelligence API as the toolbox. If you are a cybersecurity solutions provider or work in a cybersecurity department, you can decide whether you want to utilize one or two APIs separately to fill in the gaps in your systems and products or apply them all together as a complete solution.
Without further ado, let’s examine these APIs below.
Domain's Infrastructure Analysis API
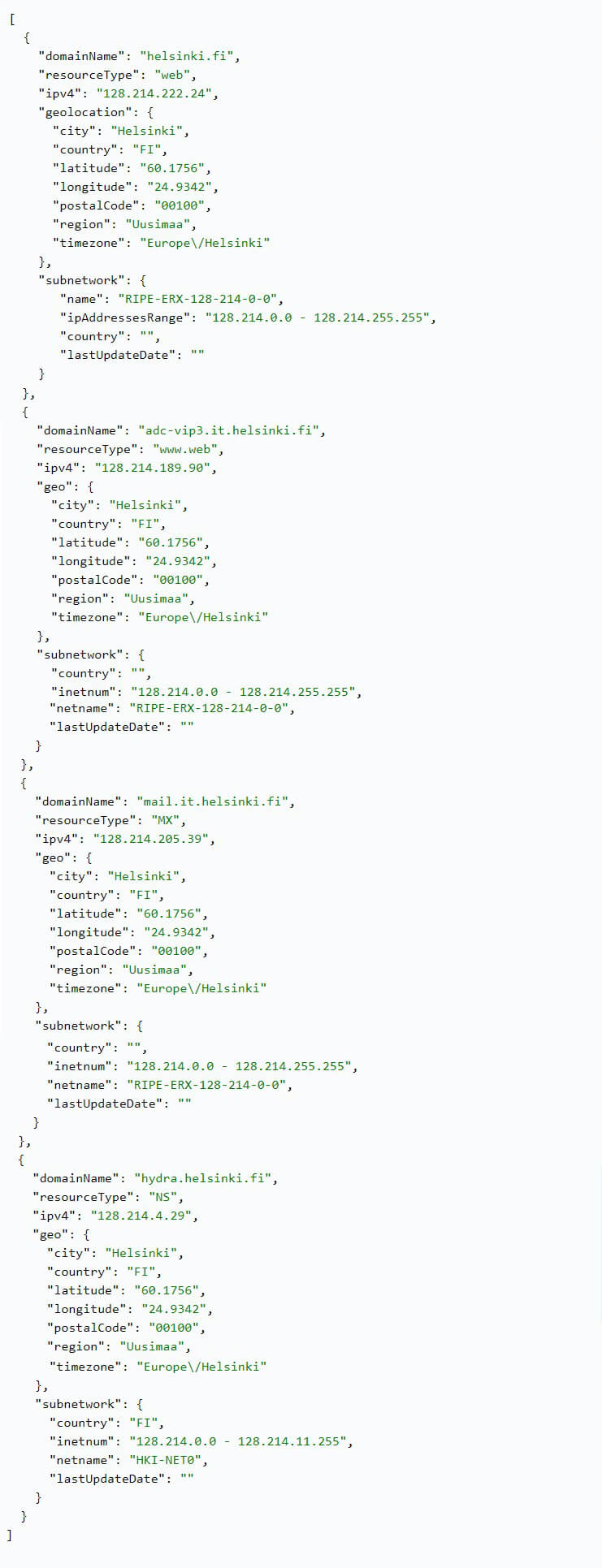
This API analyzes certain configurations of a domain, such as its web server, name server (NS), mail server (MX) and subdomains. Afterward, for each of these, the software provides details regarding their IP address, subnetwork details, and geolocation.
This information can be used by security enterprises or cybersecurity departments as part of their due diligence while preparing for merger and acquisition transactions, or when verifying the trustworthiness of a third-party provider. Users can analyze the data to learn more about how well-established an entity is and what possible vulnerabilities associated with their infrastructure may arise and what issues regarding privacy or data storage depending on the servers’ location could emerge.
It can also be combined with other details. Let’s imagine a potential typosquatting case, for instance, someone who is trying to go to the website “python.org” but instead heads over to “pyton.org”.
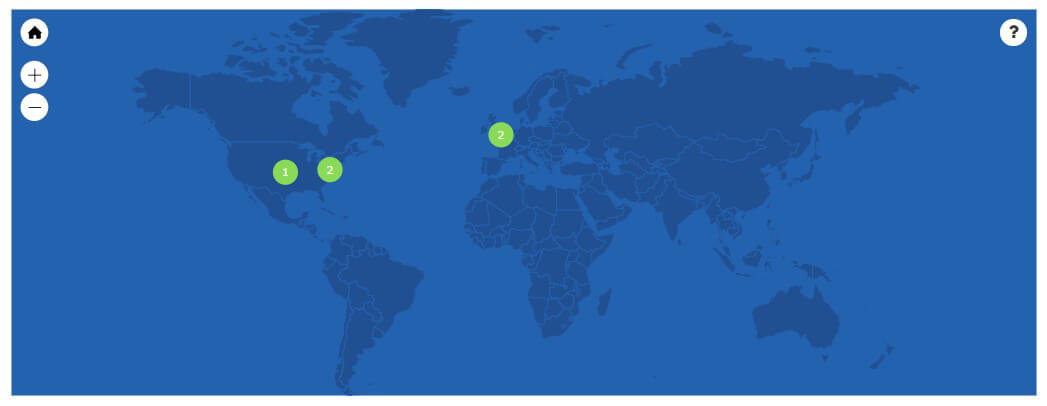
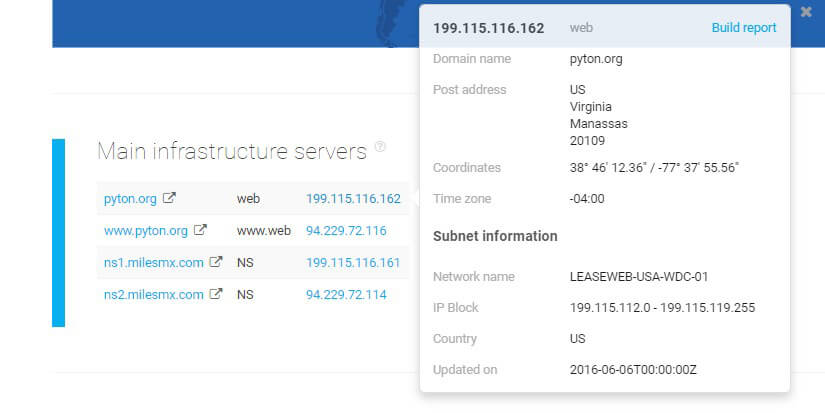
What Domain Infrastructure API reveals here is that the servers are dispersed. In the case of pyton.com this, per se, doesn’t seem alarming, however, when combined with details collected via other APIs — spotted redirects and host configuration issues, among others — such a set of information indicates that the website is not trustworthy and should be investigated further.
SSL Certificate Chain API
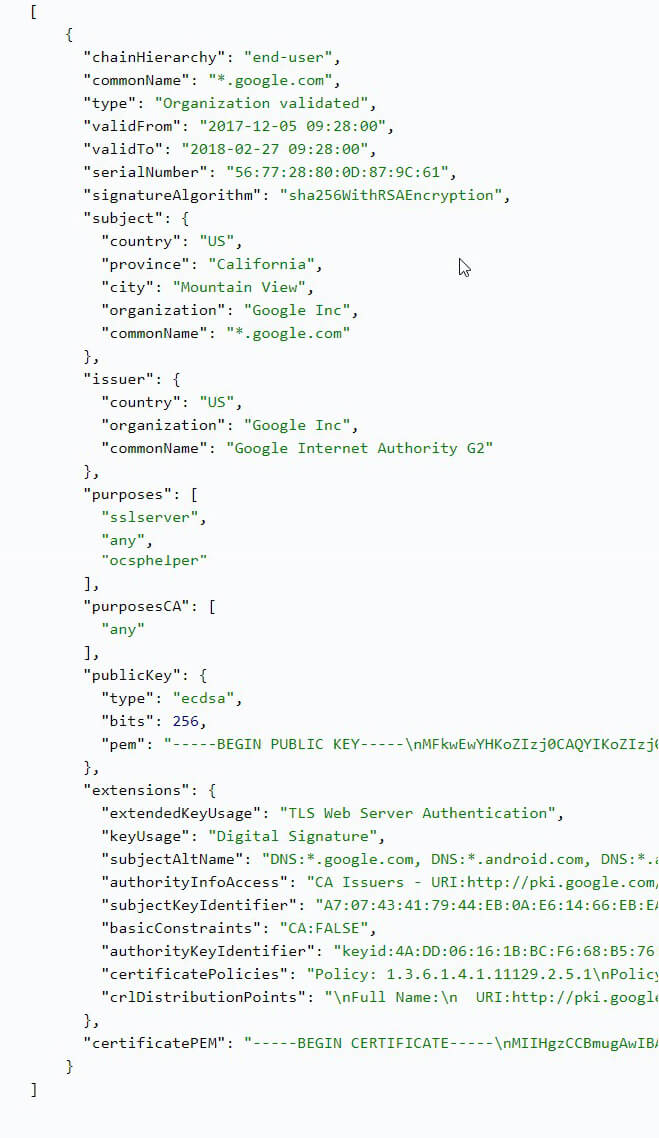
This API gathers information regarding the complete SSL certificates chain of a domain. These chains contain details needed to verify whether a website can be trusted. Upon input, the software will provide users with all certificates present in the target’s chain — analyzing both intermediate and root SSL certificates.
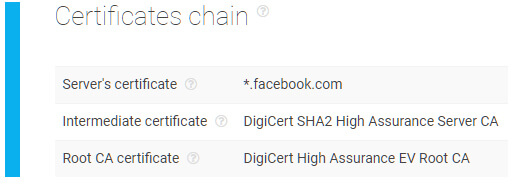
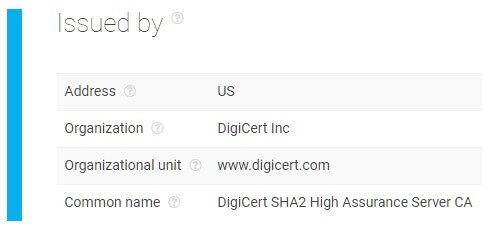
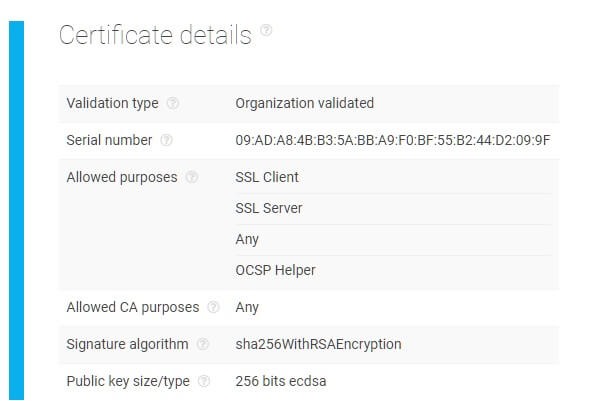
The software compares these parameters against current records to give users a report of whether the domain’s certificates were issued by a reliable source or not. There is also a section on additional certificate details which includes its serial number, allowed purposes, signature algorithm, and public key size. All of the attributes that are mentioned can be further validated by the user to ensure that every element of the chain is correct.
In the image above, the certificate chain doesn’t contain any warnings. However, if any misconfigurations with the SSL certificate chain were detected, the software would immediately flag these for review.
In fact, it is really important to spot misconfigurations not only because these might point to a malicious website but also because invalid chains can produce several issues for legitimate websites. First of all, they are normally hard to debug, plus they can lead to pages throwing out errors while browsing, which, in turn, results in poor user experience and can drive visitors away from the website.
For example, cybersecurity consulting agencies can leverage this API in order to analyze their clients’ websites and verify if they are secured with the right SSL certifications — allowing them to provide the right solution for moving forward.
SSL Configuration Analysis API
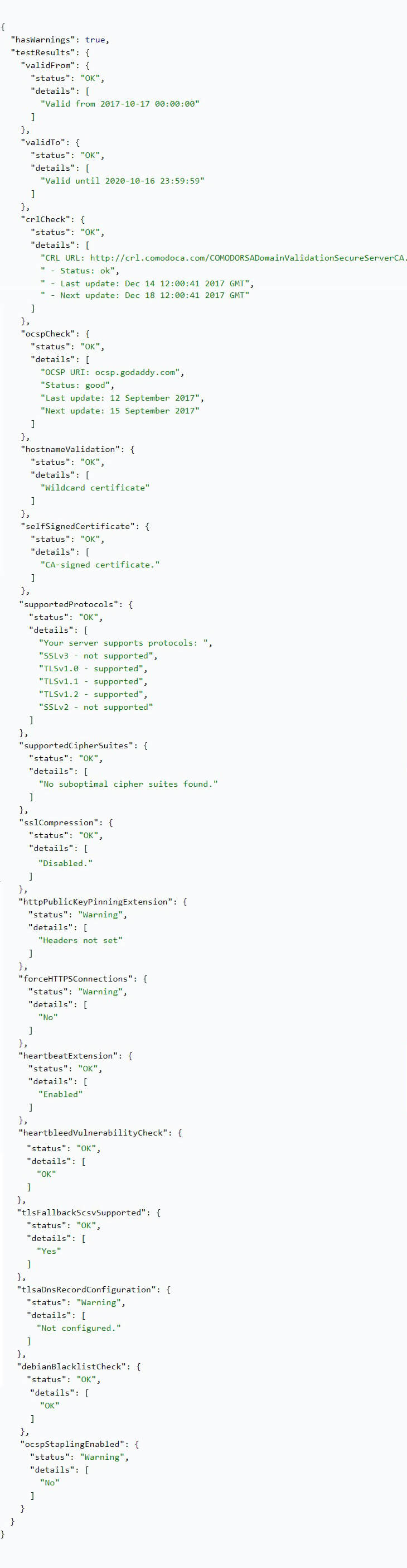
This API examines and tests the SSL connection while providing a report on how it is configured. The software collects numerous SSL parameters such as the validity dates and identifies any issues that could potentially lead to domain problems.
One scenario of this API in action can be seen with how it was able to see through a Bitcoin scam website. Criminals impersonated the futures exchange platform Bakkt by launching a fake website “bakkt.io”, inviting individuals to invest and provide their personal details for assured profits.
Although the website had already been flagged by other Threat Intelligence APIs, we ran the domain name through SSL Configuration Analysis API to see what violations it included.
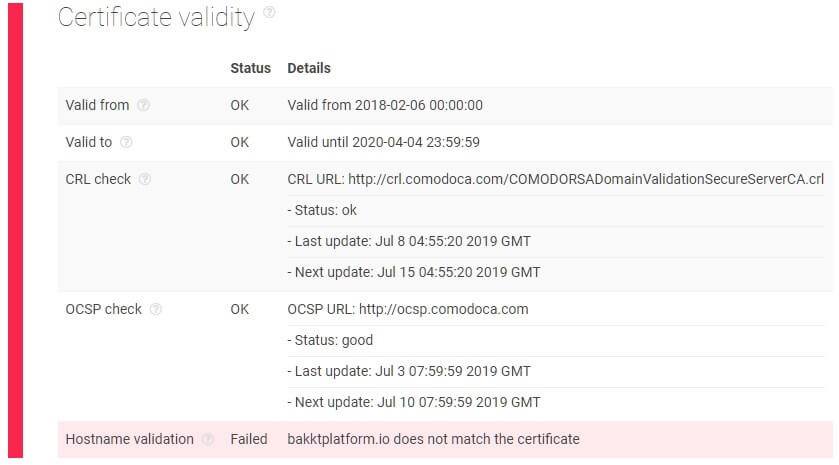
As is seen in the image, the result immediately revealed a hostname validation failure — explaining that the given domain name is referenced neither in the Common Name (CN) nor the Subject Alternative Names (SAN) in its certificate. This means that there is inconsistency in the domain’s SSL certificate validity.
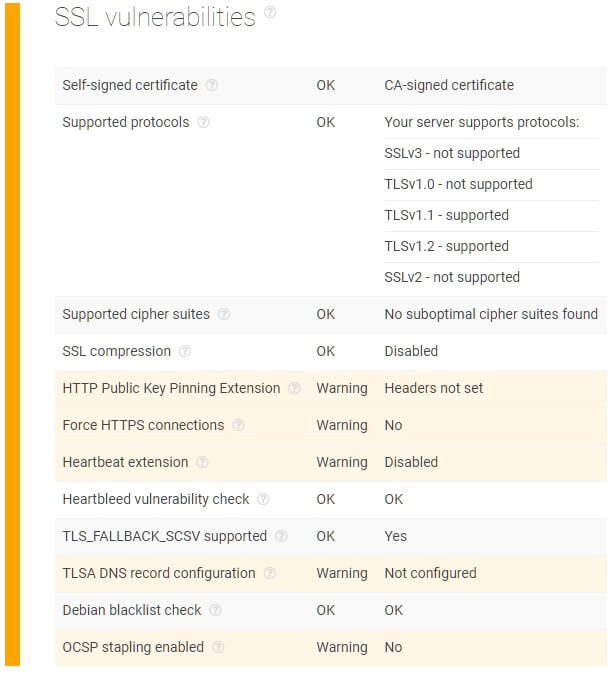
The report also shows additional warnings on this domain’s other SSL-related issues such as not forcing HTTPS connections and the Heartbeat extension being disabled. The former indicates a lack of security while the latter means that the network is open to being hit by the Heartbleed bug, which can steal sensitive information from users.
Verifying SSL configurations via this API allows cybersecurity solution providers to enrich their existing intelligence on their clients’ pages by identifying risky domains such as those with the Heartbleed vulnerability which can result in impersonation, website spoofing, and loss of sensitive information.
Domain Malware Check API
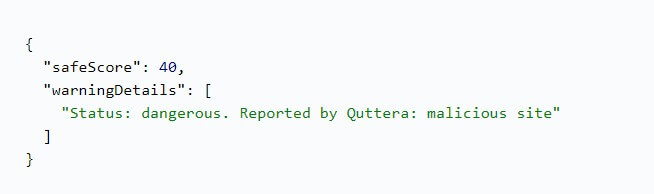
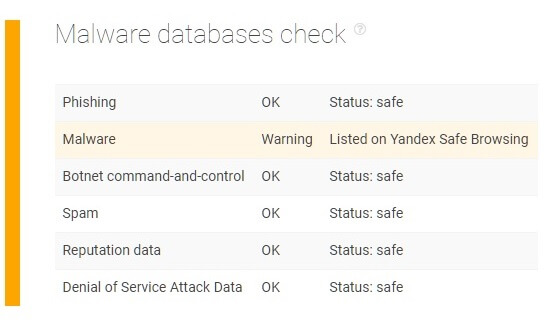
Numerous malicious domains are out there waiting for their next victim, and Domain Malware Check API can help you to reveal them before they can cause problems. The software does so by analyzing the safety score of a domain with 0 being dangerous and 100 being the safest. It also checks if the website is listed in one or more malware databases.
As is seen in the output below, this sample website has been flagged by Yandex Safe Browsing as a malicious site and warns users to avoid it. This turned out to be true as experts later discovered that the trick hackers used here was to entice people to download a pretend antivirus which actually contained harmful code.
With the help of this API, cybersecurity consulting agencies, for instance, will have the ability to perform background checks for their clients to identify websites that are safe to visit and those that are not. The product can also be readily integrated with existing software, allowing it to automatically block or quarantine low safety score domains.
Connected Domains API
This API is capable of retrieving a list of all domains that share the same hosts, IP addresses, servers, and registrant information on the Web. One of the main purposes of this is to provide users with a way to verify whether a website is connected to other malicious entities online. Such information can also help to:
- Validate third-party credibility – checking if the domains associated with a potential third-party provider are involved in suspicious activities;
- Protect reputation – sharing the same IP address range or host server with a malicious company can lead to being associated with a criminal group;
- Enforce cybersecurity – acquiring reports on all domains associated with a malevolent entity allows blacklisting potentially risky websites and preventing intrusions;
- Support investigations – law enforcement agents can immediately find connections to domains that could be part of a major cybercriminal ring. This could result in prosecution and the eventual shutdown of malicious groups.
Take, for example, this suspicious website “youzube.com”. When running it through the API, the software reveals that the domain also has equally suspicious associated domains.
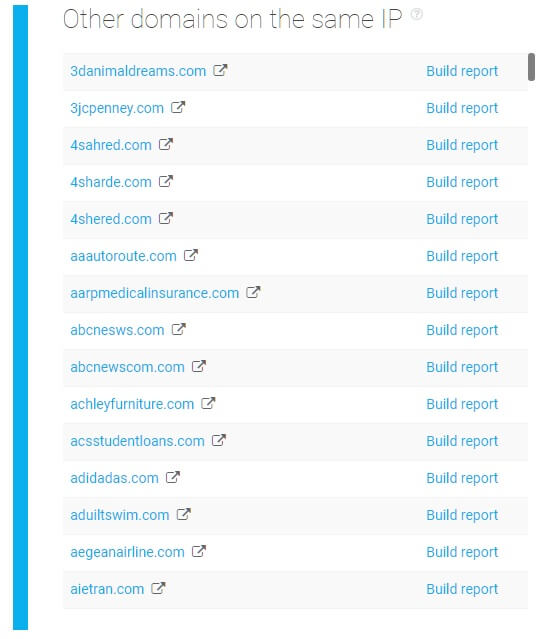
One interesting pattern is that the domain names registered by its owners are all deliberate misspellings of popular brands or websites. With this kind of scheme, it wouldn’t come as a surprise if some of them could be used for phishing, URL hijacking, or could contain malware.
Security enterprises can use the API to perform due diligence for their clients and verify if their pages are under any risk because of the potential associations with malicious domains. The information from the API can also help during risk assessment regarding the third parties with whom clients might be collaborating with, verifying if these are tied to any known shady activities.
Domain Reputation API
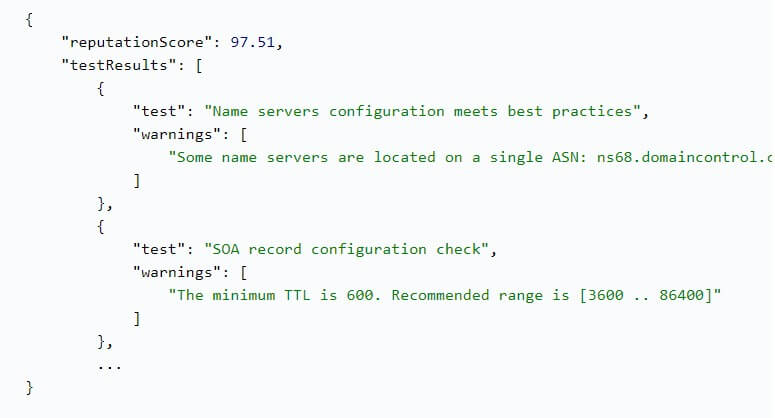
The final API in the collection offers the ability to examine certain parameters of a domain and find out its composite safety score, which ranges from 0 (dangerous) to 100 (safe). More than 120 attributes are checked and compared across various online databases to produce a reputation score for a given domain name. These measurable factors include:
- Overall website analysis – checks the potential risks associated with a website by looking into issues regarding its host configuration, file extensions, content management system, etc.
- Domain SSL certificates – the SSL chain of a given domain is validated to determine its credibility while also examining whether it is protected against spoofing attacks.
- Malware detection – includes scanning a range of malware databases to check if a domain is considered to be risky or not.
- Domain WHOIS record – the ownership information of a domain can be inspected for possible concerns such as suspicious registration dates, a registrant connected to malicious activities, registration in a high-risk country, and more.
- Mail servers – the API will look into whether an IP address or domain was blacklisted in the past due to spam or other malicious email practices, taking into account whether the target’s mail servers follow best practices such as properly configured SPF and DMARC records.
The capabilities of this API are particularly well-suited for cybersecurity solution providers looking to enhance their ability to garner advanced threat data. This product alone lets them perform a comprehensive security evaluation of their client’s web sources to lower the risk of digital threats.
Concluding Thoughts
And there you have it, a set of Threat Intelligence APIs that can provide you with the capacity to obtain insights on the threat landscape. Leveraging the capabilities behind this reliable threat intelligence software can help cybersecurity departments, security enterprises, and other organizations accomplish numerous goals moving forward.
What makes these products unique is that you can choose to acquire them individually to fill in the gaps you otherwise couldn’t patch on your own. On the other hand, these Threat Intelligence APIs can be used as a single, complete resource to expand your existing solutions and meet the growing demands of the cybersecurity market today.
If you have questions about how Threat Intelligence APIs can help your organization, please contact us at service.desk@threatintelligenceplatform.com.
Read the other articlesTo download the full article in PDF, please fill in the form.
Have questions?
We work hard to improve our services for you. As part of that, we welcome your feedback, questions and suggestions. Please let us know your thoughts and feelings, and any way in which you think we can improve our product.
For a quick response, please select the request type that best suits your needs.
Threat Intelligence Platform uses cookies to provide you with the best user experience on our website. They also help us understand how our site is being used. Find out more here. By continuing to use our site you consent to the use of cookies.