White papers
Threat Intelligence Platform Investigation #1: Payoneer Phishing Scam Hunted

It’s no exaggeration to say that cybercrime is plaguing the Internet and, consequently, business operations carried out online. As a response to that challenge, a growing number of businesses have started to move away from reactive cybersecurity practices in favor of new ones, such as threat hunting, which involves the proactive search for threats and exploitable vulnerabilities.
But even though proactivity is a battle half won, what does a threat hunt look like in practice? This report explores a real-life use case and illustrates how modern perpetrators operate as well as describing the techniques threat hunters can apply to detect and investigate foul schemes.
Table of contents
- The attack
- Hypotheses
- Host analysis using Threat Intelligence Platform
- Further investigation using Domain Research Suite
- Takeaways and concluding thoughts
The Attack
What happened
In February 2019, a user received three emails from Payoneer, a well-known company providing digital payment services, notifying him of three payments he has received. Even though the user has been the company’s client for a while, he was surprised as he did not expect any money.
After a closer look at the emails, the sender seems to be genuine — the company's customer care team. Out of curiosity, the user decides to click on the links provided in the emails and ends up on the pages requesting login details with URLs slightly different from payoneer.com.
This is, in fact, a red flag, calling for a threat hunting investigation, notably using the tools offered by Threat Intelligence Platform and WhoisXML API.
First look at the emails
All three emails were sent from a seemingly credible source — Payoneer Customer Care. At first glance, the sender’s email address (noreply@payoneer.com) and the title ‘Payoneer Customer Care’ are correct:


Yet, further examination revealed the following:
- 1. All three emails are missing the name of the person they are addressed to.
- 2. The link hovering over the “Continue” button shows similar URLs featuring the “payoneer” keyword. For example:
- http://payoneeryv.com/cgi-sys/suspendedpage.cgi?PD=celFI0m19bCmy9
- http://payoneeryn.com/cgi-sys/suspendedpage.cgi?PD=elFI0m19bCmy1
- http://vpayoneer.com/sPayoutPage/Gateway/?PD=IslFI0m19bCmy9
- 3. Quite unusually, the websites corresponding to the domains above do not have SSL encryption and are strangely spelled.
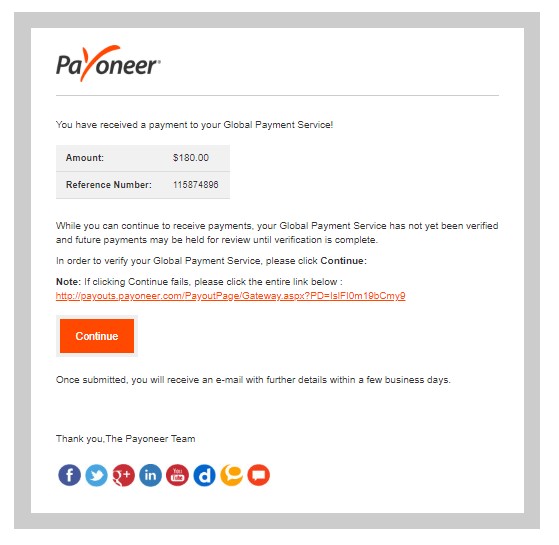
- 4. One of the links in the emails is redirecting the user to this login page:
https://payoneer.com.de/ePayoutPage/Gateway/v/?sessioniDataKey=0ebe5869-0604-4723-b1e6-e80963692ce6&state=c02629f3-b8g9-4cd5-95fc-77d3a0y5b384&client_id=GgF2F1B3J43ARMzcMuf51hProe8a - 5. Clicking on the logo on this same page redirects to yet another login page that looks like an authentic
Payoneer login page.
https://login.payoneer.com/?sessionDataKey=800c212c-ef08-48de-b607-d610dd99713c&state=180ce9db-33b4-427f-85ea-f8f21a11f872&client_id=NgK2F1B2J43ARMzhMuf5ohProe8a&redirect_uri=https%3a%2f%2fmyaccount.brand.domain%2flogin%2flogin.aspx
Hypotheses
Before the threat hunting team digs deeper into the infrastructure and details behind these pages, they create several hypotheses regarding the attack and its characteristics:
Phishing
‘Phishing’ is the most likely angle of attack here. Login credentials are what perpetrators usually aim to acquire through such communications where they pretend to be a trusted entity in order to obtain sensitive information.
Man in the Middle attack
In parallel, a Man in the Middle (MITM) attack, where communication between contacts is intercepted by a third party to listen in on the ‘conversation’ and perform illegal actions, might be at play. If this hypothesis is valid, then it’s possible that Payoneer indeed sent the original email, yet someone altered its content along the way.
Insider attack
Since the emails sender’s address looks authentic, another plausible hypothesis is that it was an intentional insider attack, for instance, conducted by someone seeking to damage the company’s reputation.
Host Analysis Using Threat Intelligence Platform
The assigned threat hunting team began verifying these hypotheses by running the suspicious domains through a threat intelligence analysis. Their purpose was to learn more about the infrastructure behind the web names. This analysis examines several parameters:
IPs and domain names
Showing how established a host is, including whether it operates via a dedicated hosting service or a shared one.
Website analysis
Revealing whether a site has poorly-written HTML code, malicious links, weak CMS protection, and other issues which hackers could exploit.
SSL certificates
Helping to understand whether a website is prone to impersonation.
Malware detection
Letting threat hunting teams learn whether the inspected domain is featured in any known malware databases.
WHOIS records
Giving access to the details provided upon the registration of a domain such as the date of registration, expiry date, contact information, and more.
Mail servers
Checking whether a website’s email system is up to standards in terms of encryption and other configurations.
Name servers
Allowing the review of name server configurations and providing information on how resilient the name servers of a particular domain are.
With this clarified, let’s examine the red flags that were uncovered.
Payoneer.com.de
https://threatintelligenceplatform.com/report/payoneer.com.de/fg87BbNSZl1. Website analysis
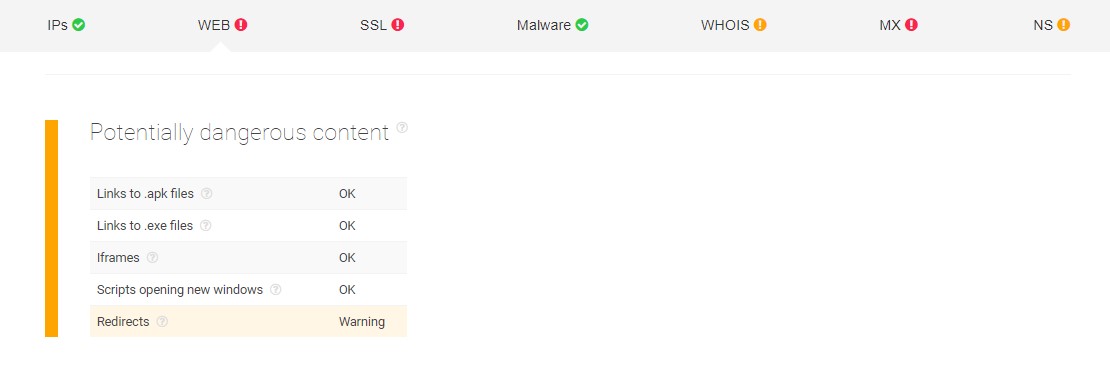
First of all, the website analysis detected redirects present on the page. The danger of these is that they can lead to potentially harmful websites containing malware or viruses.
2. SSL certificate
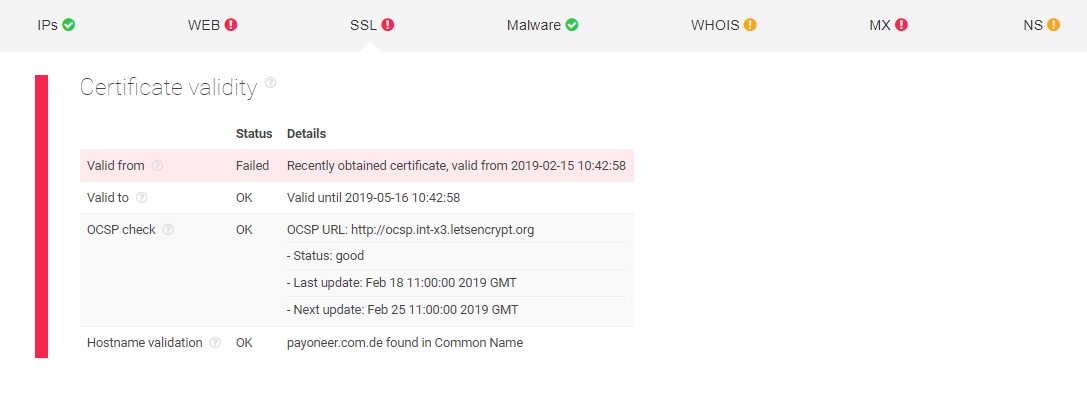
The screenshot above shows that the SSL certificate of the domain has only been acquired recently and has only been valid for a short time — also a potential sign of cybercrime activity.
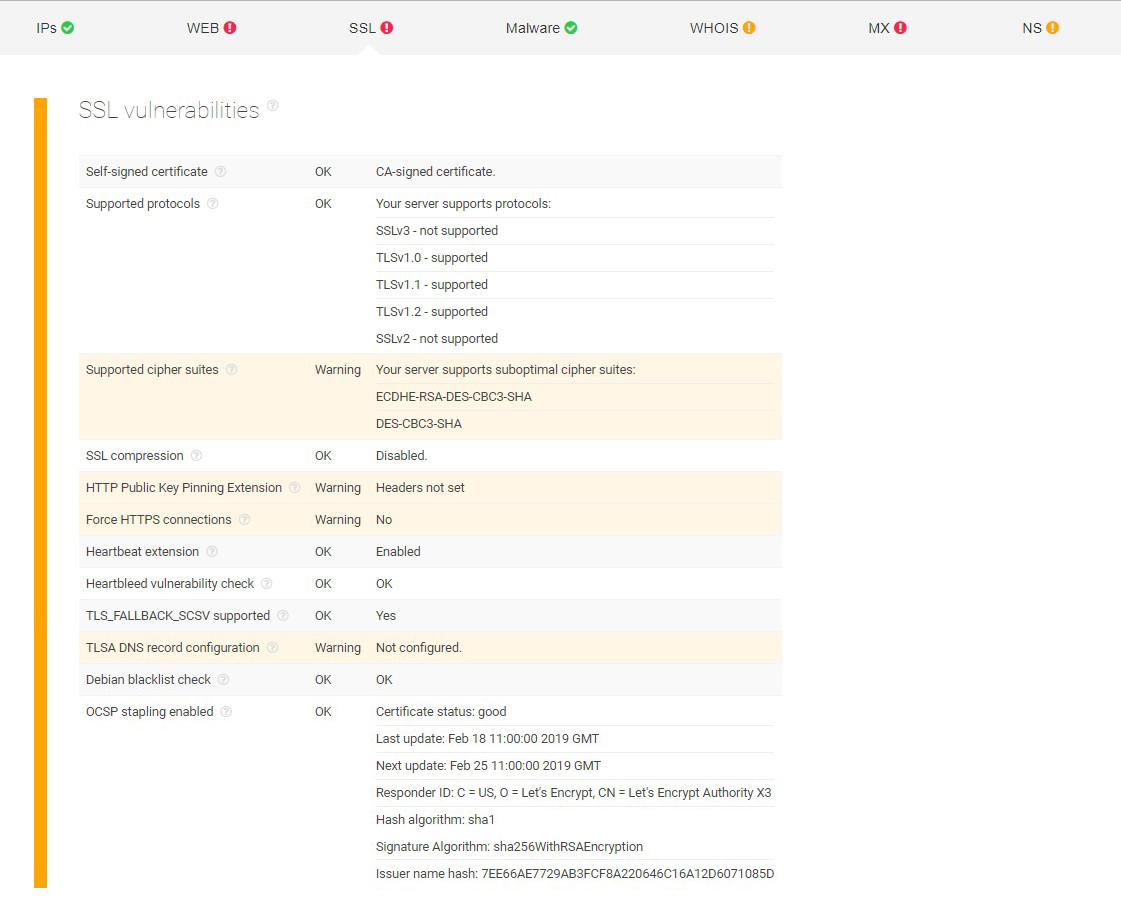
Furthermore, it was detected that the domain server supports substandard cipher suites, lacks HTTP Public Key Pinning Extension, does not have Force HTTPS connections and is missing its TLSA DNS record configuration. All of these aspects are crucial for secure network connections. Forcing HTTPS, for example, is critical for protection against cookie hijacking and protocol downgrade attacks.
3. Mail servers
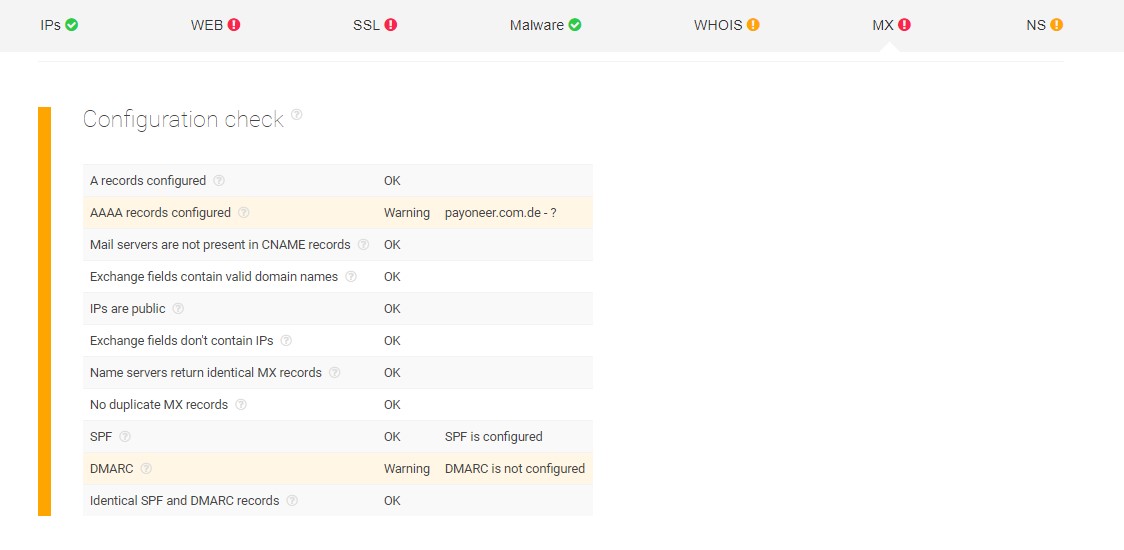
For its mail servers, the report shows that the Payoneer.com.de domain does not have its AAAA records and DMARC configured. The AAAA records play an important part in the DNS resolution process while DMARC or Domain-based Message Authentication Reporting and Conformance is used for email validation and preventing spoofing.
4. Name servers
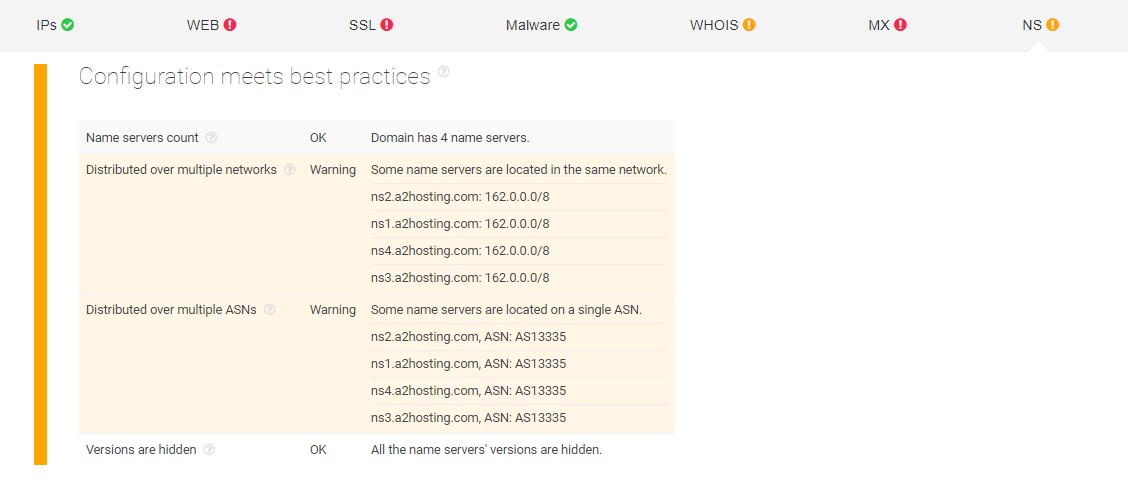
This section reports that some name servers of the domain are located on the same network and autonomous system number (ASN) rather than being dispersed to avoid a single point of failure. Such poor configurations sound strange when bearing in mind that the real Payoneer company is well-established and has a large worldwide customer base.
Payoneeryv.com
https://threatintelligenceplatform.com/report/payoneeryv.com/lbWDfc4xWj1. Website analysis
Like for the previous domain, redirects have been found (see the previous screenshot).
2. SSL certificates
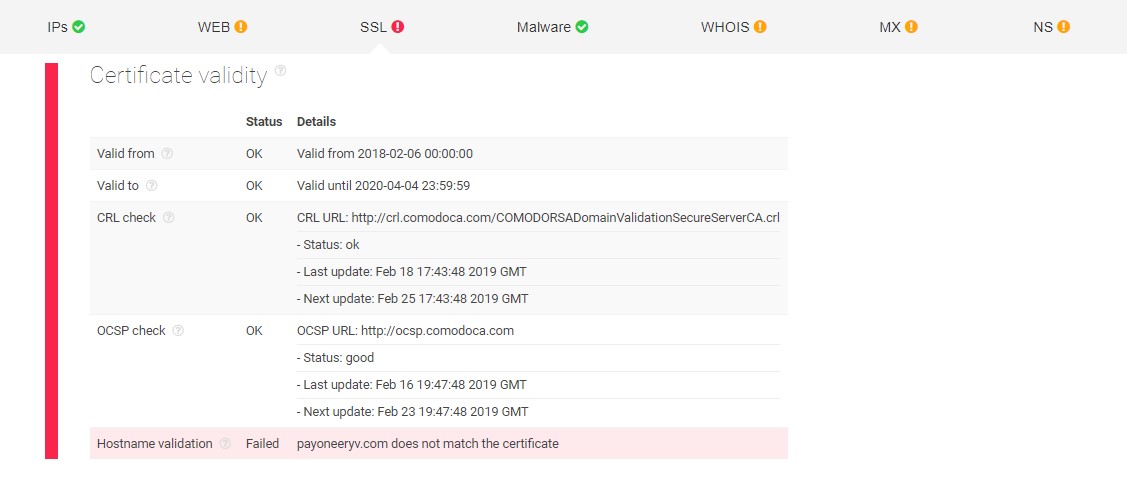
Unlike with Payoneer.com.de, this domain doesn’t seem to have a problem with the validity of its SSL certificate. However, the hostname validation has a ‘Failed’ status as it does not match the certificate provided and thus cannot be used by the target website.
3. WHOIS records
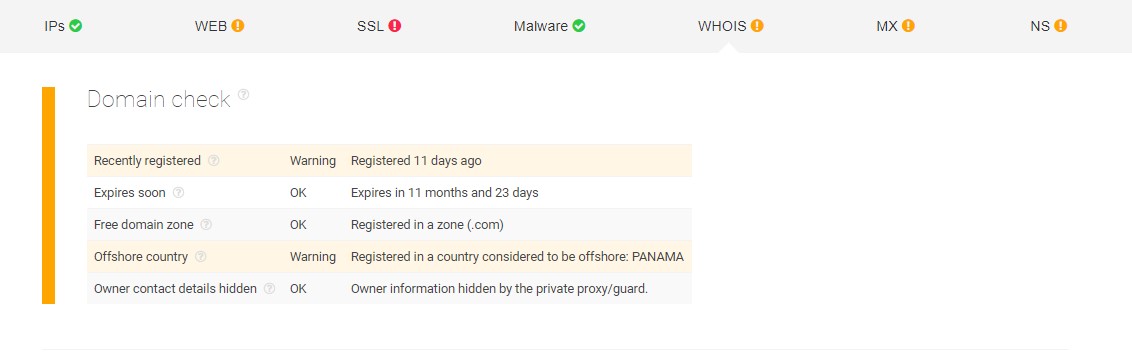
The analysis of Threat Intelligence Platform reports back that the domain has only been registered recently and its country of registration is offshore. This is suspicious since the real Payoneer’s headquarters are in New York.
Payoneeryn.com
https://threatintelligenceplatform.com/report/payoneeryn.com/2T10D2xQB11. Website analysis & SSL certificates
For its website analysis, the domain was also flagged as having redirects. And just like in the prior case, its SSL certificates came back with a failed hostname validation process.
2. WHOIS records
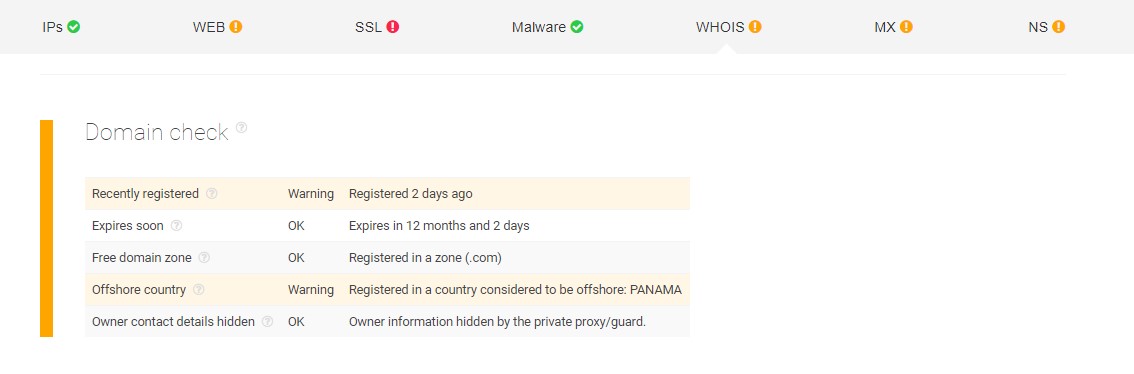
This page has similar warnings as in the above case with its domain being registered very recently (about a week apart) and the same country of registration — Panama. This may indicate that the same registrant made both of these registrations.
3. Name servers
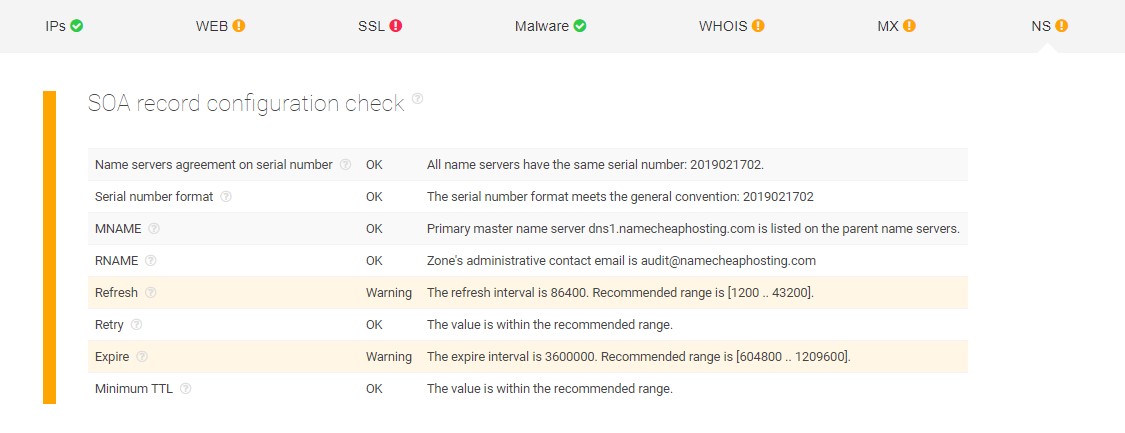
The SOA record configuration check for this website shows that some of its configurations are not up to the recommended standards. SOA records are usually employed by DNS servers when storing settings regarding how they should operate. They also include a serial number each time a change is made on the DNS records.
Vpayoneer.com
https://threatintelligenceplatform.com/report/vpayoneer.com/9dc7yKBkSAWHOIS records
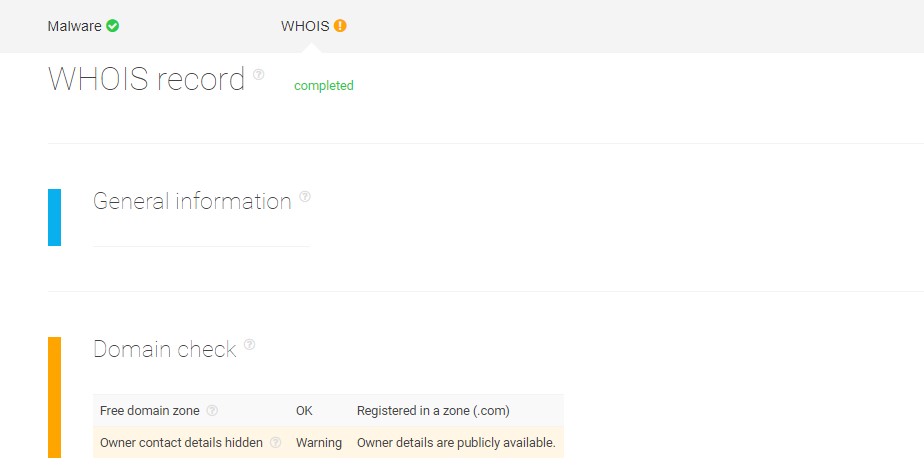
Interestingly, in this report, the contact information of the domain owners is publicly available — allowing security teams to retrieve WHOIS records and contact the owners, or forward this data to the proper authorities.
Further Investigation Using Domain Research Suite
Building on the findings accumulated with Threat Intelligence Platform, the threat hunting team continued its investigation using WhoisXML API’s Domain Research Suite, which is composed of a variety of tools:
- Reverse WHOIS search – Allowing users to identify domains based on their search terms, e.g., company name, phone number, email or else.
- WHOIS history search – Letting the user skim through a historical log of WHOIS records’ changes, for instance, to check a domain’s ownership.
- WHOIS search – Retrieving the actual WHOIS record of the target domain.
- Domain availability check – Enabling users to know which domain names are available for registration.
- Domain monitor – Tracking changes in the selected domain’s WHOIS records while keeping track of both registered and non-registered domains.
- Registrant monitor – Keeping an eye open for domain registrations, renewals, updates or expirations based on the search criteria.
- Brand monitor – Tracking newly-registered and recently-expired domains.
For the case at hand, threat hunters opted for Reverse WHOIS search, WHOIS history search, and WHOIS search to continue the investigation.
Steps of Investigation
1. Running Payoneeryv.com through WHOIS search and WHOIS history search
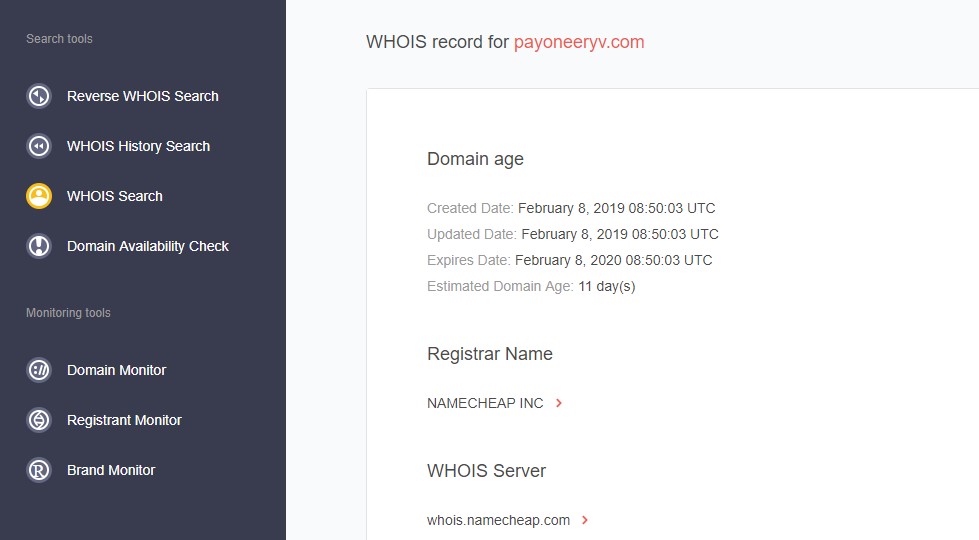
First of all, the threat hunting team learned that the website had been recently registered, adding to the initial phishing assumption. The report also reveals the name of the registrar, NAMECHEAP INC., giving a hint on who to contact for putting the website down.
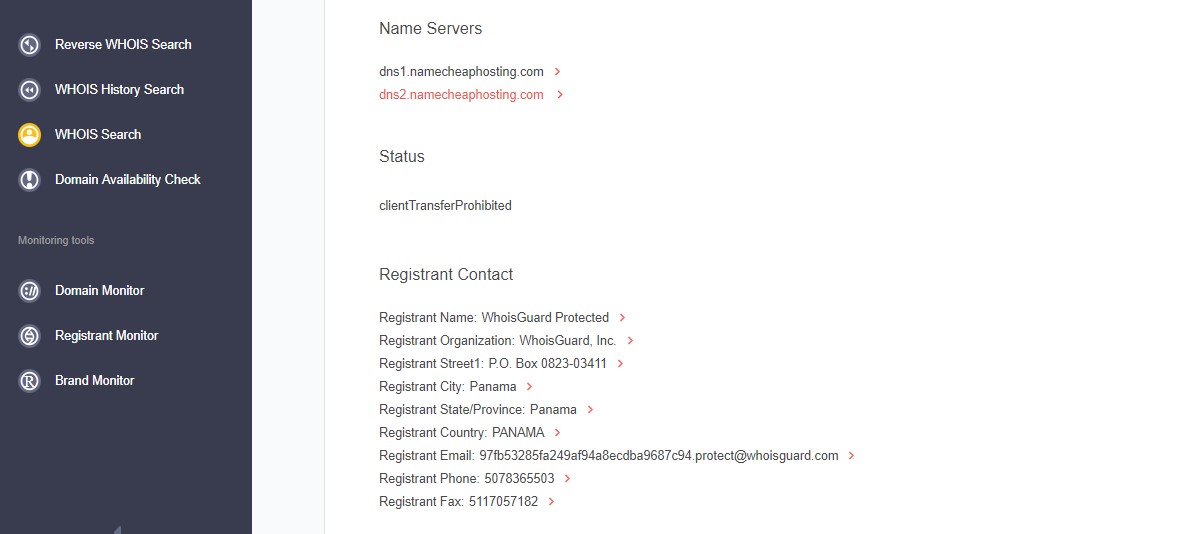
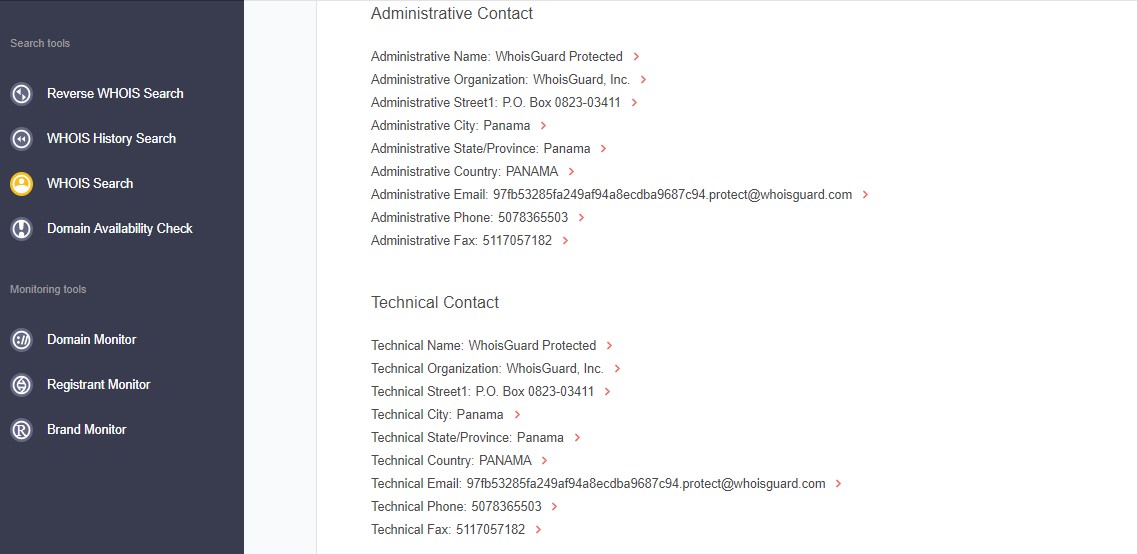
Scrolling further down, the experts are presented with the information of the registrant. Here, they notice that the registrant’s name and administrative and technical contacts are not publicly available. Instead, the details have been hidden through a WHOIS privacy protection service called WhoisGuard — a common practice for registrants who wish to keep their identity anonymous.
Note: The analysis of payoneer.com.de and vpayoneer.com led to very similar results and is, therefore, not shown here.2. Checking other possibly forged domains
The threat hunting team also leveraged the Reverse WHOIS search to obtain a list of all domains that might be forged and used for impersonation in the future. In order to do that, they input the word “payoneer” in the search filter.
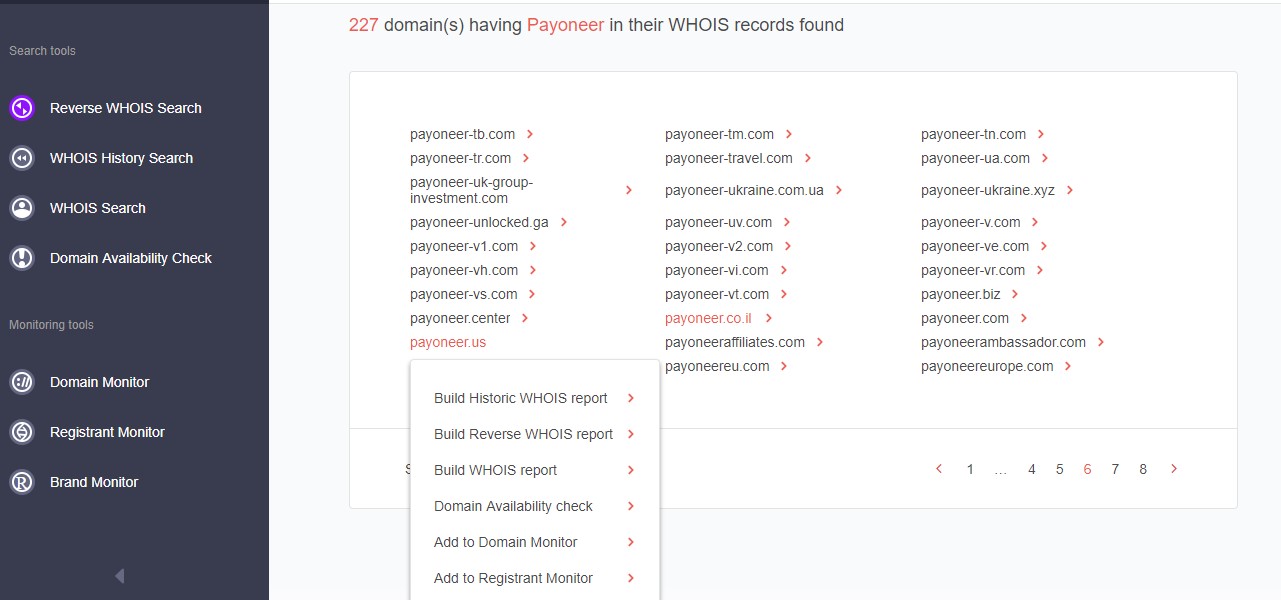
The results show that as many as 227 domains match the search parameter. For every match, threat hunters can develop reports and run it through other tools. In this specific case, to verify which of the domains might be fake, specialists make use of the WHOIS history search and WHOIS search features.
Take, for instance, the Payoneer.biz website. It has a similar name and an uncommon TLD, so the experts want to assess the likelihood of it being forged and decide to explore this in detail as per the following screenshots:
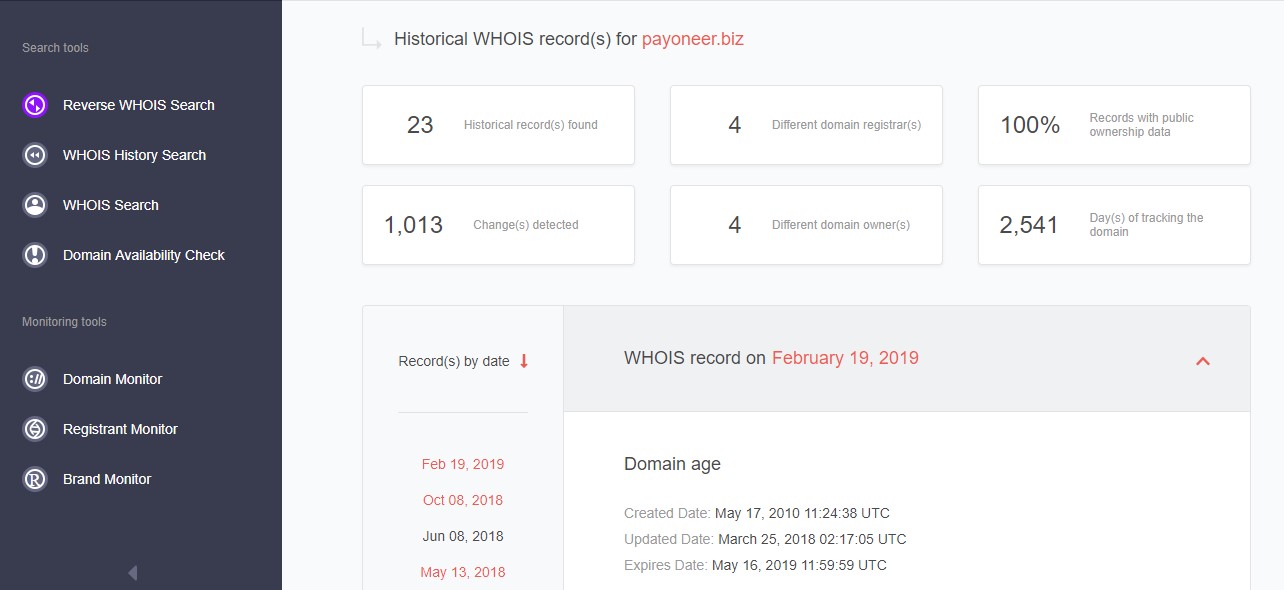
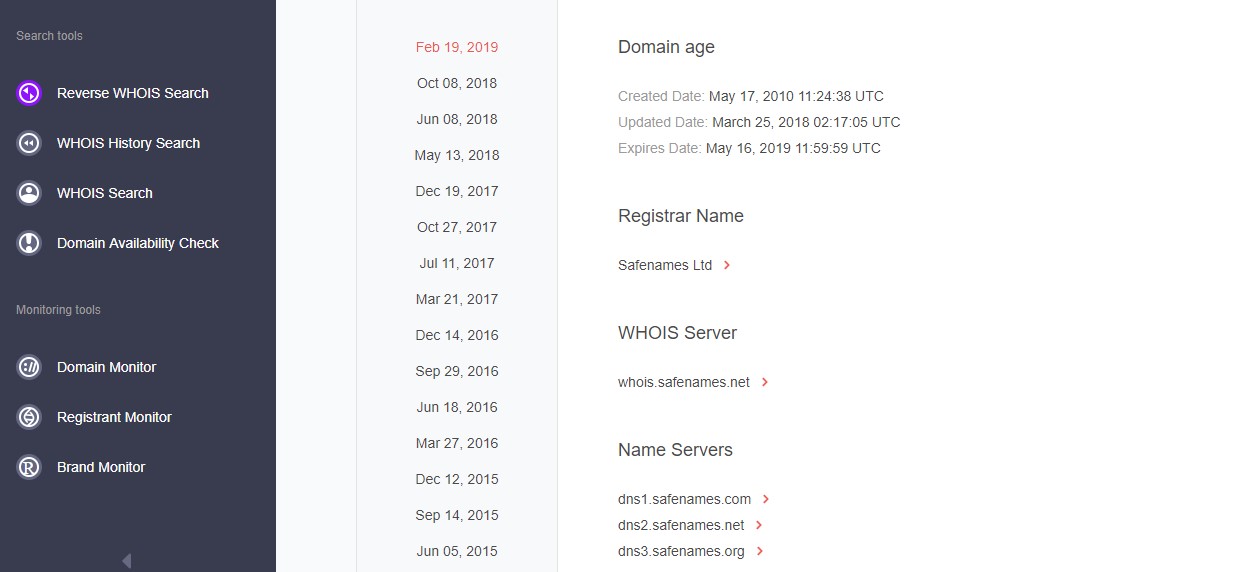
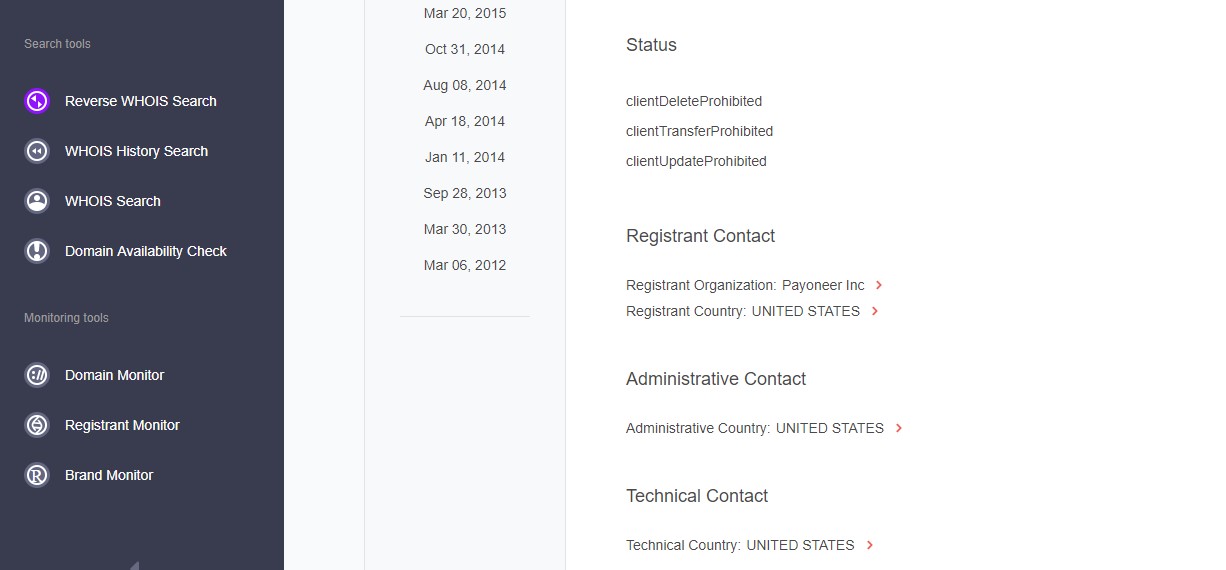
The team finds out that the site was created in 2010. That’s a long time ago, making it either unlikely for the domain to be malicious, or likely to have been recently seized.
The WHOIS history search also reveals historic records showing the real registrant organization (Payoneer Inc. or the owner Yuval Tal) which is identical to that of the authentic Payoneer.com domain — indicating that Payoneer may have registered it for another purpose like trademark protection.
Takeaways and Concluding Thoughts
As a result of a thorough investigation, threat hunters concluded that they were dealing with a phishing attack. The evidence of that included recently registered domains with similar sounding names but slightly different spelling, messages not personally addressing the recipient and prompting immediate actions, websites’ configurations not up to standards, and hidden domains owners’ contacts.
Let us emphasize a few critical points. First of all, whenever a malicious incident occurs, it is critical to conduct a threat intelligence analysis so that users can learn more about the perpetrators’ infrastructure and identify patterns in their behavior. It is also important to explore the WHOIS records of suspicious domains in order to assess the likelihood of them being dangerous.
Secondly, both individuals and brands targeted by such schemes can benefit from recognizing other potentially harmful domains. For instance, they can utilize the Domain Monitor functionality offered by WhoisXML API to keep track of new domains with similar-sounding names and receive alerts every time one is being registered.
Read the other articlesTo download the full article in PDF, please fill in the form.
Have questions?
We work hard to improve our services for you. As part of that, we welcome your feedback, questions and suggestions. Please let us know your thoughts and feelings, and any way in which you think we can improve our product.
For a quick response, please select the request type that best suits your needs.
Threat Intelligence Platform uses cookies to provide you with the best user experience on our website. They also help us understand how our site is being used. Find out more here. By continuing to use our site you consent to the use of cookies.