Blog
Uncovering Botnets Through Domain Reputation
Introduction
Although they represent just one of the many cyber threats in existence today, malicious botnets are some of the most significant threats to internet security.
Botnets, aka ‘bots’, date back to the dawn of the internet itself. Hosting applications and performing repetitive tasks, bots have leveraged the distributed nature of the internet in tasks such as search, collecting, and the delivery of information. Malicious bots however, surreptitiously employ and infect target computers as part of a ‘zombie’ network, managed at a distance under the control of a malicious cybercriminal.
Once established, a botnet can launch attacks against even more computers, against unsuspecting users, against government agencies and just about every type of organization out there. Once unleashed, a botnet can leverage the power of thousands, hundreds of thousands, and even millions of computers in one command. In its wake, a botnet attack and related activities can create the following disruptions:
- Collect private information from infected users;
- Further spread botnet malicious payloads, cryptomining threats, ransomware, and more;
- Create a flood of email spam that can reach millions around the world;
- Denial of Service (DoS) and Distributed Denial of Service attacks;
- Distributed brute force hacking tasks.
To put it mildly, malicious botnets possess a massive potential for unfettered cybercriminal activity, which can be difficult to track and protect against, proving to be among the most significant threats on the internet today.
Thanks to the efforts of law enforcement and major technology providers, successful attempts have been made to stop and take down botnets. However, cybercriminals have also evolved their tactics, employing dynamic domain techniques and a rapidly changing foundation called a fast-flux network. One of the best ways to uncover and detect botnet activity is through domain reputation research. Initiated within the activities of a threat intelligence program, domain reputation information is constantly updated, and can uncover the launch of networks by bot operators before they pose a threat to the organization.
The purpose of this paper is to help educate technology practitioners, Internet users, technology executives and the security community on the importance of monitoring domain reputation to be protected against botnets and botnet-related activity. This knowledge gap discussion focuses on the validity and power of activity research and the context-based effect of publicly available WHOIS data.
Awareness Through Domain Info
It may not be obvious to the uninitiated, but the information behind domains is a valuable source in the hunt for security threats. Billions of times a day, domain information is exchanged between users around the globe, connecting their devices to applications, email, and secure computing resources. This information is highly trusted and it is built into every single application and resource in existence. Criminals see this trust level as their opportunity, plying attacks, infections, fraud, and countless other acts through its systems.
WHOIS and DNS
When a domain is registered, the WHOIS standard dictates what information is required to submit the desired domain into the worldwide domain name registry. Leveraging DNS, the Domain Naming System, the two components build a virtual directory of every domain on the web. The details of how to connect to systems with a set domain exist at one level of this directory, while in the other, a deeper set of details dictate what information exists behind the scenes, such as who registered the account, contact details, dates of registration, and, ultimately, who owns the domain. It’s not a perfect system as the information collected is vaguely accurate, rarely audited, and regularly abused or neglected by registrants. This information is also not updated regularly.
Despite the imperfections within WHOIS data, the information within presents a valuable tool in the hunt for malicious cyber activities. Organizations can use this data to protect themselves and their customers from fraud, ransomware, malware, crypto-mining attacks, spam networks, and other forms of malicious online activity.

Risk-Aware Domain Reputation
The Importance of Domain Reputation
Domain reputation is an effective tool that is regularly utilized in email and network security. This construct gives practitioners the information needed to decide whether they trust the transaction of information to and from domain-based networks. Whether it’s basic emails, networking communications or any combination of activities, domain reputation is an integrity checkpoint that eliminates the need to dig into internet address blocks or individual internet protocol (IP) addresses. Internet Service Providers (ISPs), hosting providers, email providers, and others leverage domain reputation along with IP reputation to monitor and protect their infrastructure and services.
Early botnet detection is achieved by dynamically detecting changes that occur in DNS and WHOIS information, leveraging domain reputation and other levels of information within assessment. As botnet controllers are busy creating the infrastructure for their botnet systems, detectable anomalies in the DNS and WHOIS systems can quickly tip off security defenders about a building threat. By catching this early in the lifecycle, protecting against botnets becomes a proactive activity aimed at detecting existing behaviors and correlated with up-to-date information on registered domains.
How Does It Work?
Domain reputation lookup exposes risk components in the information collection phase. Analysis takes place using the following incorporated example factors:
- Recently registered
- Expires soon
- Free domain zone
- Offshore country
- Owner contact details
When correlated with other factors, such as a malware database check, the conclusions are undeniable. Malware database checking may include:
- Phishing
- Malware
- Botnet command-and-control warning
- Spam
- Reputation data
- Denial of Service (DoS) Attack Data
Further available information includes the collection of DNS query information, analysis of the domain structure, subdomains, registrar information, zone information, and network characteristics. The security practitioner can use this information to analyze and rank the risk level of log-based events and create a custom reputation model. Using domain reputation and a tool that can explore these factors, something as innocuous as a domain lookup in a protected environment can prompt a protective action.
Signs of a botnet
With the Threat Intelligence Platform (TIP), the existence of a botnet can be detected and confirmed by using several points of information. The TIP platform is a robust, up-to-date tool that allows organizations to collect, research, and analyze information about potential threats. It makes extensive use of domain reputation factors, along with pertinent information that helps in this analysis.
The TIP platform is typically used in a total threat analysis program to further explore suspicious issues and create organization-specific threat profiles using the event information collected. It features an API for continual, routine, and automated lookups, but it is useful as a web-based research tool as well.
How Does It Work?
Let’s look at a suspicious domain. Assuming the domain in question came up in local DNS queries requested by critical company systems, this is something you’d want to research.
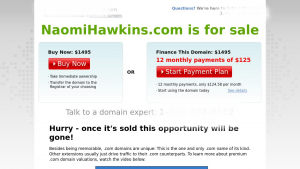
A parked web page appears, and at first glance, it appears to be an innocuous domain, but the tool tells us more.
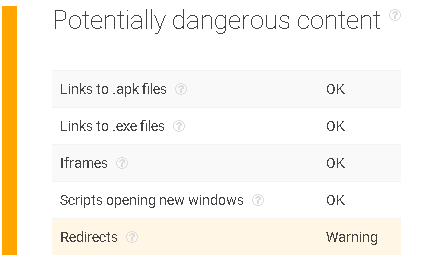
Potentially Dangerous Content
This bit of information begins to raise the suspicion levels. Although it has passed the majority of checks, there is a redirect warning.
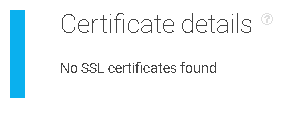
SSL check
SSL detection was passed with no warnings, but that’s only because the site has no SSL certificate in the first place. If a certificate was found, pertinent information such as expiration, issuing authority, and date provides context for a possible threat.
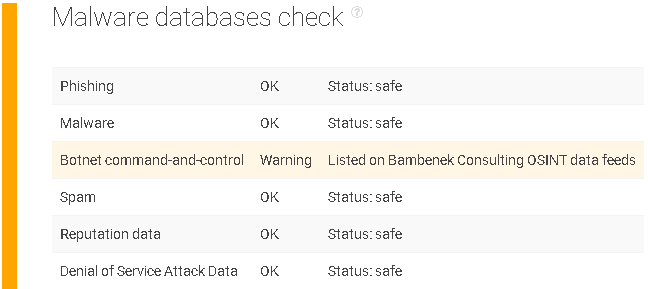
Malware Databases Check
Here’s where things get interesting. The domain comes up as part of a known malware data feed as a botnet command-and-control host. This data feed is quickly validated, meaning you can see that at some point, the domain was correlated to botnet activity.
Threat Assessment
Every assessment process is different, as should be the case with each organization, but common threat indicators help the organization to come up with their own evaluation.
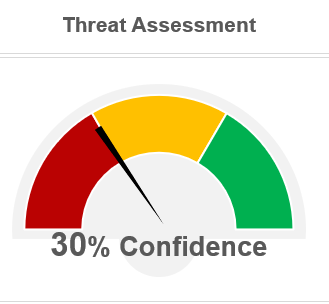
While the domain in question did not raise any red flags across the board, there is enough here to justifiably decide to blacklist this specific domain.
Specifically:
- A business-justified reason to connect to this domain has not been presented.
- The malware database check shows a red flag.
- The lack of SSL certificate means the domain hasn’t been validated in any tangible way.
- The content check and redirect indicate something lying beyond when visiting this page.
Analysis
This domain reports a history of botnet activity and warrants blocking.
Although it currently appears to a parked domain webpage that is currently registered and hosted through Amazon, cybercriminals are adept at rotating assets of networks, domains, and domain states. Due to this history and the impression of a non-active webpage, there is little value in maintaining access to this domain.
Key Takeaways
- Domain Reputation is a valuable tool in the fight against malicious botnets.
- Specialized tools help uncover pertinent DNS and WHOIS information, relationships, and other discoveries.
- Early data research is one of the best methods of detecting potential botnets.
Have questions?
We work hard to improve our services for you. As part of that, we welcome your feedback, questions and suggestions. Please let us know your thoughts and feelings, and any way in which you think we can improve our product.
For a quick response, please select the request type that best suits your needs.
Threat Intelligence Platform uses cookies to provide you with the best user experience on our website. They also help us understand how our site is being used. Find out more here. By continuing to use our site you consent to the use of cookies.