Blog
Your 2019 Security Task List

Getting better through better threat detection and response
As we kick off another year, security practitioners look for information to make their environments safer, and easier to protect. Incidentally, most environments need better ways to enhance security to add value and capability, both technologically and practically.
We could go down the track of highlighting all the stuff that is easily found in SANS and CISSP sources, and we encourage you to check an endless array of sources for what common things you need to do and put together. We’re doing things differently, to get you in and out of here, to get you the information you need for the right mindset and for your horizons to open to different solutions.
Systems and Network security have been a challenge for as long as they first existed. As technology progressed, capabilities undoubtedly got better, but the goalposts keep on shifting. Today, securing the modern environment is more difficult than ever before, thanks to a good deal of coinciding factors.
Attackers are Getting Better
Attackers are using more sophisticated and scalable tools than ever before. We live in an age where DDoS attacks can be purchased on the web, thus eliminating the need for technical knowledge. Pick your target, pay for it, schedule it, and the rest, as they say, is history.
As “script kiddies” and amateurs abound, sophisticated attackers are also scaling and transforming their efforts, challenging the best of security products and practices across the landscape.
That Powerful Infrastructure
A big change that has happened in that traditional infrastructure continues to fade in favor of scaled, hyperconverged, virtual, and cloud-based systems. This new construct of infrastructure presents a radically different concept of security perimeter, especially when it is compared to the four-wall boundary concepts of the past. Today’s security practices focus on identity and access controls built into the environment itself rather than hardening and rulesets alone.
Business and Security
Once relegated to the domain of information technology teams, security is now the concern of business units throughout the organization. We’ve all seen security incidents, massive breaches, and loss of data reported in the news. When those things happen, heads roll and insurance is paid out, causing companies money and reputation.
Your 2019 Task List
Find Analytics
By all means, if you are at a nexus point where a technology refresh or opportunity is at hand, it is important to score analytics high up on your list of features. Security teams benefit from heightened analytic capabilities and these features are becoming more common and more powerful everyday tools. In addition, intelligent tools integrate orchestration and automation features that match up well with modern cloud and virtualized environments.
Integrated Security
One of the most promising trends in the industry today is the ability to leverage integrated security throughout the infrastructure product set. Virtual appliances and firewalls are turning up throughout the fabric options that comprise today’s infrastructures. Azure features a variety of pre-built security images, third-party firewall products, and features such as monitoring/auditing. AWS hosts a similar lineup of security-focused applications. Essentially, security controls are now available wherever infrastructure exists, protecting access throughout the mobile, flexible nature of cloud, hybrid, and multi-cloud environments.
Find Threats with Domain Threat Investigation
For all of the sophisticated, intelligent tools out there, in many situations the best defense systems should implement domain threat investigation techniques. In an age where countless pools of domains are registered and leveraged daily, the power of leveraging deep information about domains and the networks behind them is critical. Best of all, this process is simple and enabling security teams with this valuable tool reaps scalable rewards.
Domain Threat Investigation analysis can disclose a variety of factors such as time, certificate validity, parent/child relationships between domains, historical registrant information, crawl analysis, domain activity, domain status, registration information and more. That information is built into our Threat Intelligence Platform. After all, data is only useful when it is multi-dimensional and non-linear.
Case in point: Let’s say you found a domain from system logs (example: chansfound.com) that you want to investigate, perhaps, from a web server, or log-on attempts on the system itself. What you’re looking for is a potential prelude to an attack. Are you dealing with a malicious domain? If it doesn’t turn up there, is it possible that the domain is affiliated with other malicious domains?
- 1. Submit to TIP

- 2. Gather and review alerts

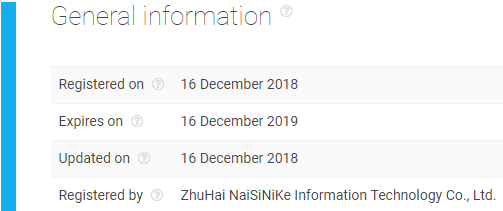
- a. General Info:
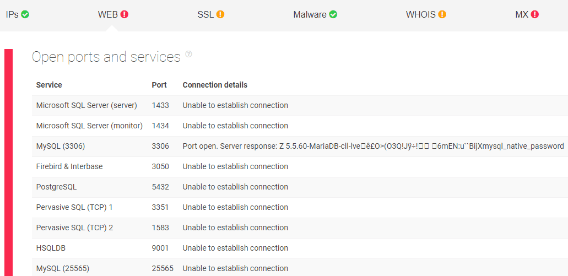
- b. Web Alert: ports and services
Specific concern:
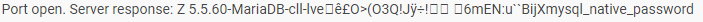
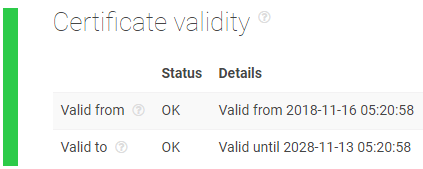
- c. SSL Alert:
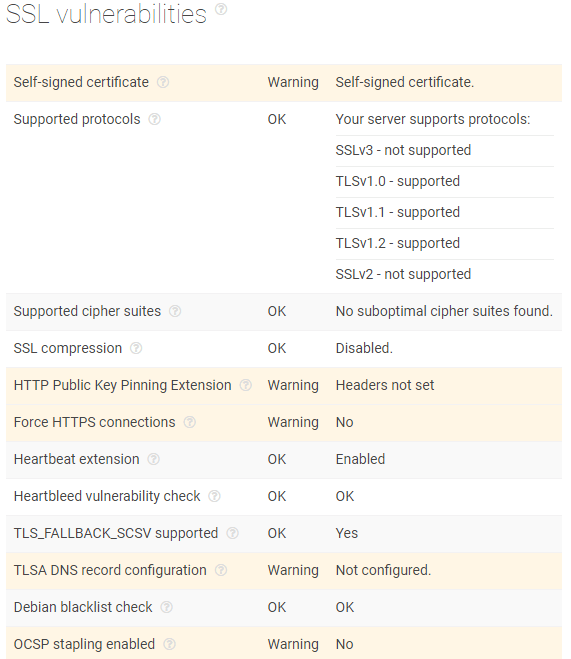
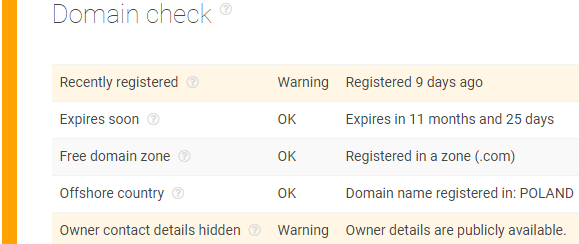
- d. Domain check:
- e. Mail
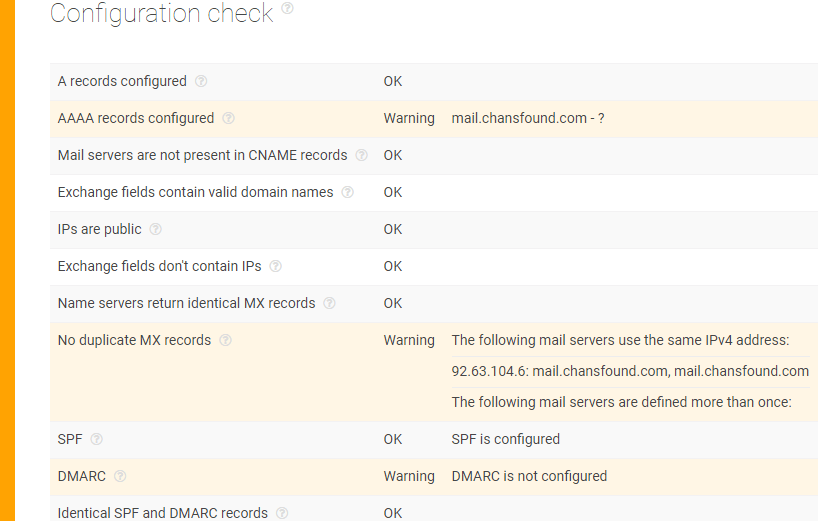
- a. General Info:
- 3. Analyze:
- a. We have a domain that was registered on December 16, 2018;
- b. The certificate is self-signed, and valid from 11/16/2018 to 11/16/2028;
- c. The site features strange MySQL strings;
- d. The mail information for the domain is suspiciously tied to unreachable entries.
- 4. Score:
Although it isn’t registered in malware or spam blocklists, the domain chansfound.com should be considered highly suspicious.- A self-signed certificate, with a 10-year validity and with a one-year backdate in comparison to domain registration is a red flag.
- Mail configuration information that cannot be found is of major concern, another red flag.
- Strange MySQL ports and services are suspicious and should be also seen as a red flag.
- 5. Act:
At a minimum, traffic to and from this domain should be closely monitored at all points of egress and ingress. Vigilant organizations should block this traffic.
Research value
One of the most effective information technology security tools in the year ahead is the investigative power of organic, custom information-driven threat intelligence and the powerful, up-to-date information that is built into the Threat Intelligence Platform. Actionable data means better security – as simple as that.
As practitioners hunt threats in the wild throughout the year, practical security measures are expected to be in high demand in the face of ever-increasing threats. Access to intuitively presented and compiled information can help quickly discover issues and protect assets accordingly, as events are taking place. When attacks are multi-faceted or multi-layered, remember that common behavior shows how attackers are looking to leverage and scale attacks, which limits the number of sources they might execute their attacks from. It takes effort to create attacks and their vectors, making isolating incidents to networks and domains a mission-critical security priority.
Threat Intelligence Platform is designed to produce rapid insights, with detailed drill-down information for the best possible analysis of threats that are tied to domains, certificates, networks, and more. Better still, as part of a complete threat intelligence program, the information and research gleaned from the program means that the risk is relative and specific to what is going on within your enterprise and not generalized threat information.
The list (and your assignment) goes like this:
- 1. Demand and score analytic capabilities;
- 2. Look for integrated security features in prospective and existing products;
- 3. Implement customized threat intelligence information into your security process.
Thanks for the ride, we’ll be here throughout the year with more tips, so don’t forget to sign up for a trial account!
Read other articlesHave questions?
We work hard to improve our services for you. As part of that, we welcome your feedback, questions and suggestions. Please let us know your thoughts and feelings, and any way in which you think we can improve our product.
For a quick response, please select the request type that best suits your needs.
Threat Intelligence Platform uses cookies to provide you with the best user experience on our website. They also help us understand how our site is being used. Find out more here. By continuing to use our site you consent to the use of cookies.