The identification of malicious IP addresses serves at least two primary cybersecurity goals from the opposite sides of the fence. First, it protects your online properties from blacklisting. It has become pretty standard for companies to share an IP address with other users due to the saturation of the IPv4 space. And if you happen to share a host with a malicious domain, yours may end up on a blocklist, too.
Second, one way of preventing a cyberattack is by identifying all of its possible sources, given a single indicator of compromise (IoC). One such identifier is an IP address that you often find listed on publicly accessible threat databases.
Not every product in the market today list down all of the IP addresses a domain resolves to, information that is crucial in determining the nature of a given domain name, including yours. But with the right cyber threat intelligence feeds such as the Threat Intelligence Platform (TIP), companies stand a greater chance of avoiding risks. TIP subjects domains to several tests, including a comprehensive check of IP resolutions with its built-in IP reputation API, to ensure their security. This post mainly shows how TIP can help companies avoid domain blacklisting and becoming the next cyberattack target.
Avoid Domain Blacklisting by Identifying Bad Neighbors
While most companies don’t employ IP-level blacklisting for fear of blocking the access of legitimate users along with those that are malicious, organizations that established zero-trust policies might. That said, it is crucial for businesses that use shared IP addresses to ensure that they don’t use the same IP addresses as bad actors do. TIP can help with that. Find out how below.
Let us say that your company recently received a complaint from one of your loyal customers saying that he can’t access your website. You scoured the Web for more information and found that your IP address 185[.]120[.]221[.]28 (highlighted in gray) appears on AbuseIPDB’s IP blocklist.
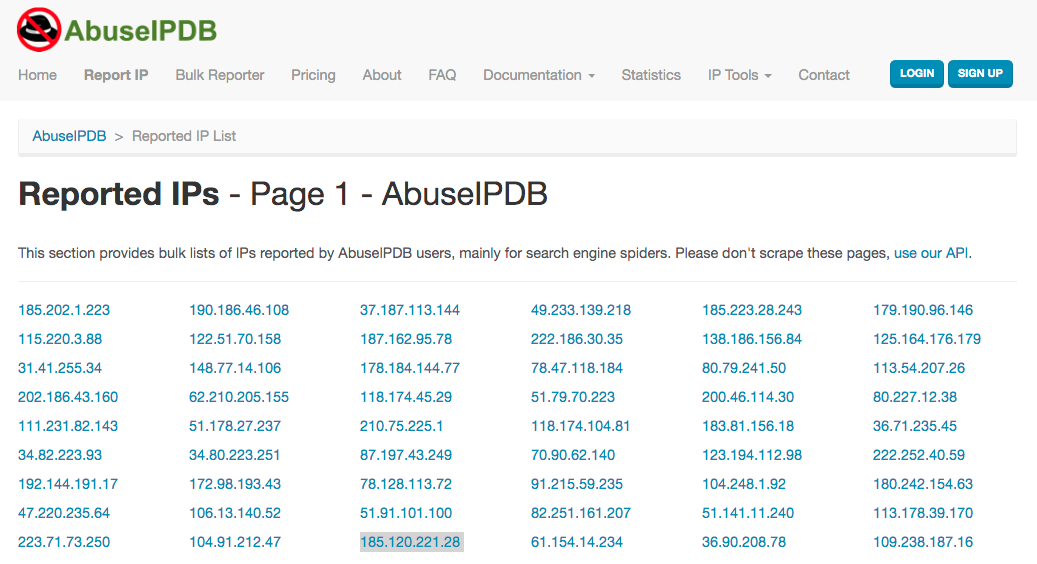
You need to get off the said blocklist if you want visitors (old and new alike) to keep coming to your website. Otherwise, your company will lose the much-needed revenue. But first, you need to prove that your site is threat-free. You can use TIP for that. Subject your domain to a TIP analysis. Based on the malware check, tzar[.]ir (your domain in this hypothetical scenario) is indeed malware-free.
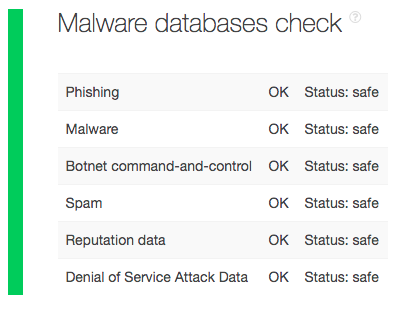
You can keep a copy of your domain test as proof of your website’s good standing.
Now, you know that your site uses a shared IP address. One of your neighbors, therefore, could be the reason for its blacklisting. TIP can help with that as well. Subject your IP address to a TIP query to identify all of the domains you share it with. The platform should give you a list of five domains. One of them, of course, is yours.
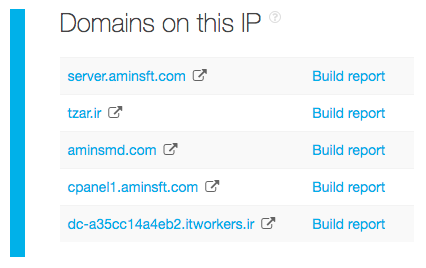
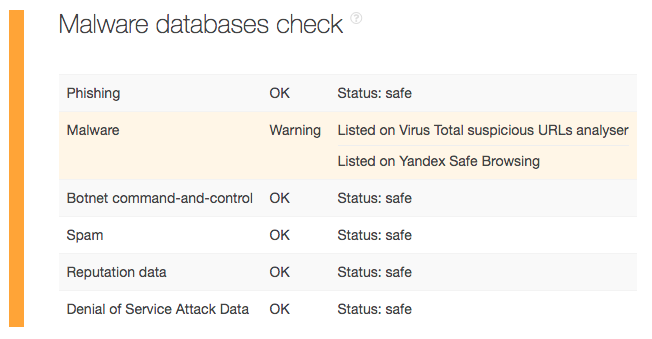
Build a report for each domain on the list to get to the bottom of the issue. After further scrutiny, you will find that your domain tzar[.]ir, aminsft[.]com, and itworkers[.]ir are innocent. The culprit listed on VirusTotal and Yandex Safe Browsing is aminsmd[.]com.
Now that you’ve completed your investigation, you can ask your Internet service provider (ISP) to assign you a clean IP address. Make sure to submit the evidence you gathered. The succeeding switch in IP address should solve your website inaccessibility issues.
Pinpoint All Other Possible Threat Sources with a Single IoC
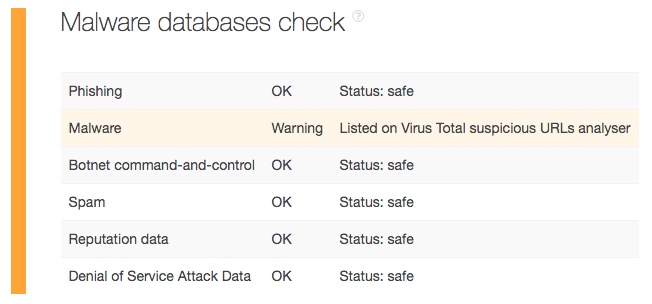
This time, let’s move on to keeping your corporate network safe from external threats. Let’s say, for instance, that your company’s security solution detected an intrusion from a user coming from hkrevolution[.]club. You can subject the said domain to a TIP analysis, which would tell you that it is a malware host listed explicitly on VirusTotal.
The TIP analysis through its IP reputation API would also provide you a list of all IP addresses and domains connected to the malicious domain.
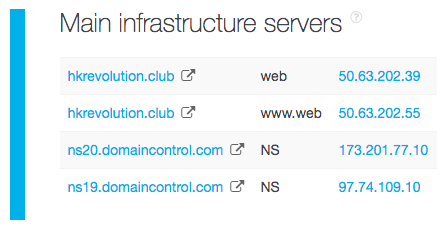
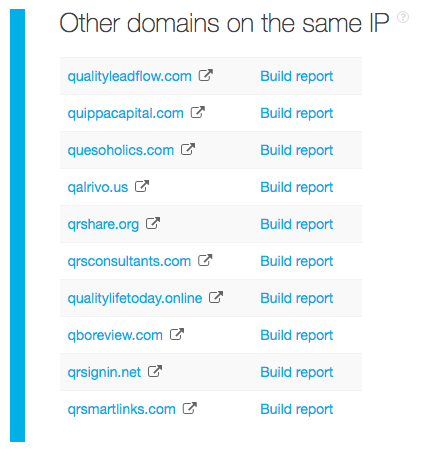
To ensure protection from all other threat sources related to this specific attack, you can build a report for each IP address and domain. Should any of them prove malicious as well, block access to them immediately. Our deep-dive, for instance, yielded these additional threat sources, which probably need to be blocked, too:
- 50[.]63[.]202[.]39: Listed on VirusTotal as a malware host. See the full TIP report here.
- 50[.]63[.]202[.]55: Listed on VirusTotal as a malware host. See the full TIP report here.
A Web search using the domain and IP addresses as keywords revealed ties to the so-called “TwoSail Junk” or “Poisoned News” watering hole attack, which targeted iOS device users in Hong Kong. The attackers used the malware LightSpy to infect their victims’ devices.
---
As you’ve seen, an IP reputation check is one of the ways to avoid blacklisting and stay safe from known and unknown threat sources. Without constant monitoring and vigilance, falling prey to the perils brought on by malicious IP addresses is highly likely. To beef up your cybersecurity posture and maintain a good domain reputation, therefore, you need to use the right cyber threat intelligence feed that has a built-in IP reputation API such as TIP.