Email remains the most widely used means of communication between organizations. On average, 53.65 billion legitimate emails are sent daily. With that, unfortunately, also comes a startling fact—an average of 302.99 billion illicit emails or malicious spam ply the Internet every day. These statistics clearly show the importance of monitoring spam emails while on their way to corporate users’ inboxes.
One way to do that is by screening senders and messages for threats using robust analysis products such as Threat Intelligence Platform (TIP), probably as part of existing email security solutions and processes. Read on to find out how.
6 Checks the Threat Intelligence Platform Does to Protect Users from Malicious Spam
Threat analysis tools like TIP can run various tests on email senders’ domain infrastructure to ensure that recipients are not communicating with dangerous hosts. The platform explicitly scrutinizes:
1. Mail Exchanger (MX) Records
To effectively receive emails, an organization needs to correctly fill in its domain’s MX records, which specifies how to route messages through the Simple Mail Transfer Protocol (SMTP). The MX record identifies the mail server responsible for accepting emails addressed to the recipient’s domain.
This TIP check allows users to ensure that no legitimate emails sent to network-connected users fall through the cracks. Attackers sometimes don’t bother to properly configure their inboxes because they don’t expect replies from their victims in the first place. Therefore, the absence of an MX record or it having incorrect settings can be a sign that the sender is a malicious entity.
2. Mail Servers
All valid email addresses should have a corresponding mail server. And that mail server should be able to respond within a specified amount of time via an SMTP connection.
TIP checks if the sender’s domain has corresponding mail servers and if these communicate as they should. The absence of such or their misconfiguration could be indicative of an attack. The platform also checks if the mail server is present in 106 available blacklists. Inclusion in any of these lists is a telltale sign of malicious dealings.
3. Domain Validity
All mail servers should connect to domains, and the specified names should be valid, i.e., resolve to an IP address in the DNS. Otherwise, users won’t be able to communicate with anyone.
TIP checks if a suspicious email came from a user with a working domain name, which means that any message originating from an inactive or nonexistent domain will be red-flagged by the platform.
4. IP Addresses
TIP lists the IP addresses associated with the sender’s domain. When subsequently queried, these IP addresses can be checked for connections to malicious activity and their presence on several blacklists. Note that IP address mismatches (when put through forward and reverse checks) can also indicate malicious activity.
5. Name Servers
Different name servers should have the same MX record. If that isn’t the case, then you may be involved with a rogue server. TIP checks for this as well, assuring users that they are dealing with legitimate email messages.
6. TXT Records
The ubiquity of malicious spam now requires organizations wary of email spoofing to check if messages adhere to Sender Policy Framework (SPF) and Domain-Based Authentication, Reporting, and Conformance (DMARC) requirements. If they don’t, there’s a likelihood that the emails came from malicious sources.
TIP checks that SPF and DMARC are properly configured according to standards as these are practical email validity tests against threats. The platform also ensures that the senders’ domains don’t have identical SPF and DMARC TXT records.
Now that you have a better idea of how TIP helps organizations ward off spammers, let’s look at a case to see it in action.
Putting the Threat Intelligence Platform to the Test: The Dharma Ransomware Spam Campaign
About a month ago, researchers discovered a spam campaign spreading Dharma ransomware in Italy. Based on the report, we learned that the attackers sent emails with a malicious attachment (Dharma file) disguised as an invoice to potential victims. As a result, users who downloaded and opened the file lost access to specific files on their computers.
We obtained the email address getdataback@fros[.]cc from another Dharma ransomware attack report. Note that organizations should block access to all known email addresses related to the threat. We subjected its domain to a TIP query and found that it indeed has malware associations and so users should immediately delete all messages coming from senders using the domain fros[.]cc, along with others on the list.
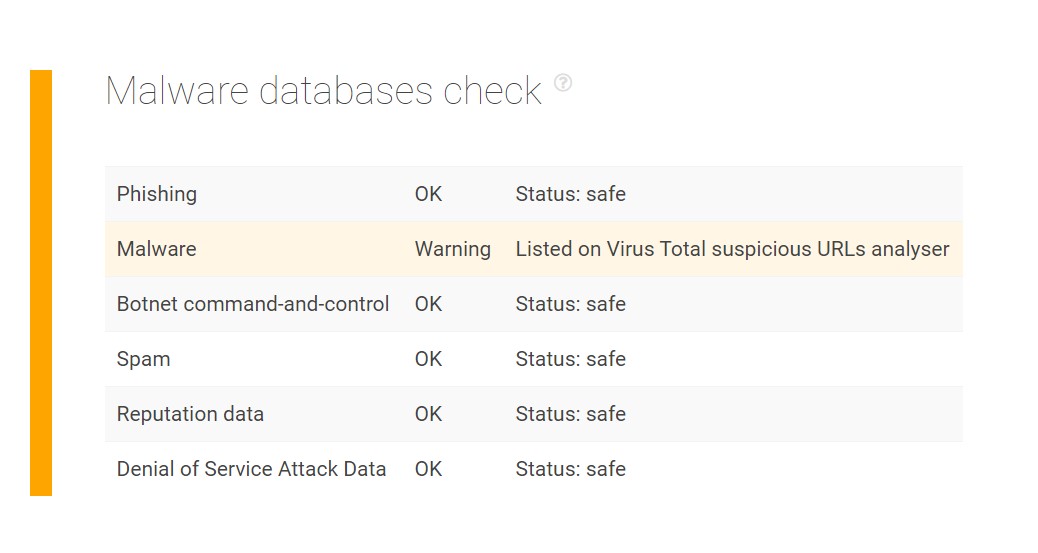
The mail server check for the domain of another email address from the same list berserk666@tutanota[.]com revealed a warning (note the difference in top-level domain [TLD]), which could be indicative of connections to malicious activity as well:
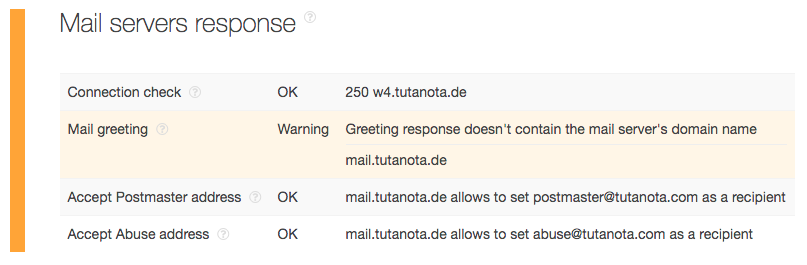
---
Threat analysis tools like TIP can serve as an additional line of defense against malicious spam emails that typically carry much more damaging payloads. In this case, that comes in the form of Dharma ransomware, which can successfully disrupt a user’s or an entire organization’s operation.
