As Heraclitus said, “change is the only constant thing in this world.” More than 2,000 years later, this statement couldn’t be more accurate, especially in the world of cybersecurity. New attack vectors materialize out of nowhere to the point where an email from your CEO has to be scrutinized before employees can act on the message. Cybersecurity experts thus have no other choice but to step up their game, and they surely can’t afford to accidentally ignore a possible attack vector in their cyber monitoring and defense.
For this reason, cybersecurity professionals should be on the lookout for the best threat intelligence feeds. The case in point is Threat Intelligence Platform (TIP), which takes into account several areas that attackers could penetrate, including an organization’s domain and IP infrastructure. The platform checks for vulnerabilities in a given domain’s mail and name server configurations, WHOIS domain records, Secure Sockets Layer (SSL) certificate chains, and IP infrastructure. In the process, it also helps organizations check a website for malware so employees can avoid accessing domains and IP addresses that attackers weaponized.
How does it all work, you may ask? Let’s take a closer look.
From Domain Reputation to Checking a Website for Malware
One of the most helpful features of TIP is that it automatically computes a domain’s reputation score. This means that security teams don’t have to spend too much time weighing the safety of visiting a website on a given domain or IP address. The platform does that for them instead. It computes a domain’s reputation score based on several factors, including:
- Checking a website’s content for malware presence
- Host configuration
- Connection to other domains
- SSL certificates, connections, and configuration
- WHOIS domain record
- IP infrastructure
- Mail server (MX) configuration
- Name server (NS) configuration
As you can see, it would require valuable time and effort for cybersecurity professionals to examine these aspects of a domain or an IP address one by one. With TIP’s help, however, security teams can quickly find out whether or not a domain or IP address is secure.
They can also use the platform in conjunction with their existing security information and event management (SIEM) systems. That way, when the domain reputation score falls below a predetermined minimum acceptable rating, they will be alerted instantly. A low domain reputation score means that accessing the domain or IP address in question is risky.
The subject of domain reputation and scores has been tackled extensively already in several of our past blogs, notably looking at the benefits and specific use cases like stopping defacers and uncovering botnets. For the rest of this blog, let’s take a look at a more specific aspect—how TIP can help check a website’s domain or IP address for malware with a concrete example.
Avoiding a Chase Bank Copycat Domain Tied to Malware
Among the favorite lures that threat actors use to carry out crimes are emails from supposed banking institutions. In 2019 alone, threat actors registered more than 1,900 potential phishing domains in the sector, showing a 14% increase from 2018. And since domain registration is not very restrictive, anyone can register domains and use them in phishing attempts connected to malware attacks.
In PhishTank, for instance, we found the domain https[:]//chase-financial9w[.]com/home/myaccount/index[.]html. An average Internet user would think that this link leads to the website of JPMorgan Chase Bank, one of the largest financial institutions in the U.S. Potential victims could key in their login credentials, under the impression that they are logging into their accounts, and download a malware file.
However, organizations can protect their employees from such occurrences with TIP. The platform’s analysis detected that the domain is a malware host according to Google Safe Browsing. Below is the screenshot of the analysis.
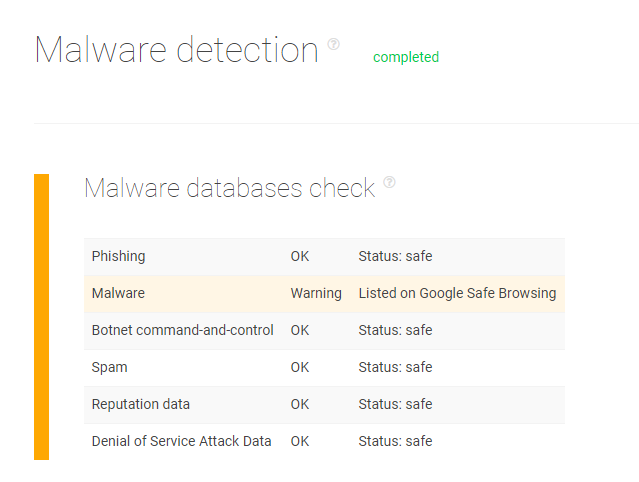
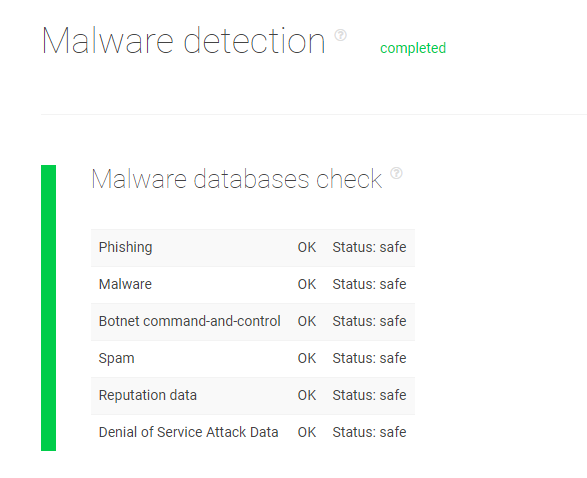
We ran the legitimate Chase Bank domain https[:]//chase-financial[.]com/home/myaccount/index[.]html on TIP, in comparison. It isn’t on any malware or threat database.
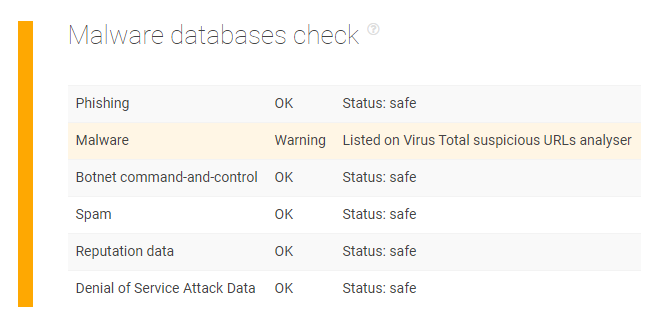
Avoiding an Emotet-Distributing IP Address
TIP also enables organizations to prevent malicious IP addresses that threat actors use to inject ransomware and other malware into vulnerable systems and networks. For instance, we ran the IP address 69[.]43[.]168[.]245 on the platform. This IP address is a reported indicator of compromise (IoC) tied to an Emotet Wi-Fi spreader, and TIP’s malware check also found that the IP address appears on VirusTotal.
---
Attackers make use of IP addresses and domains to commit their crimes. Filtering malicious IP addresses and domains would, therefore, fend off threat actors and protect organizations and their employees from becoming the next cyberattack victim.
An effective way to do this is to rely on Threat Intelligence Platform (TIP) to monitor domain reputation and check a website’s domain or IP address for malware. Better still, cybersecurity specialists can automate the process by integrating the platform into existing systems.
